`TryHackMe` : LazyAdmin CTF
TryHackMe : LazyAdmin CTF
In this part of our quest to becoming proficient Linux pen testers we need to put our expertise against an introductory level box, which supposedly has a lazy admin looking after it - should be straightforward enough I hope:
Obligatory nmap scan:
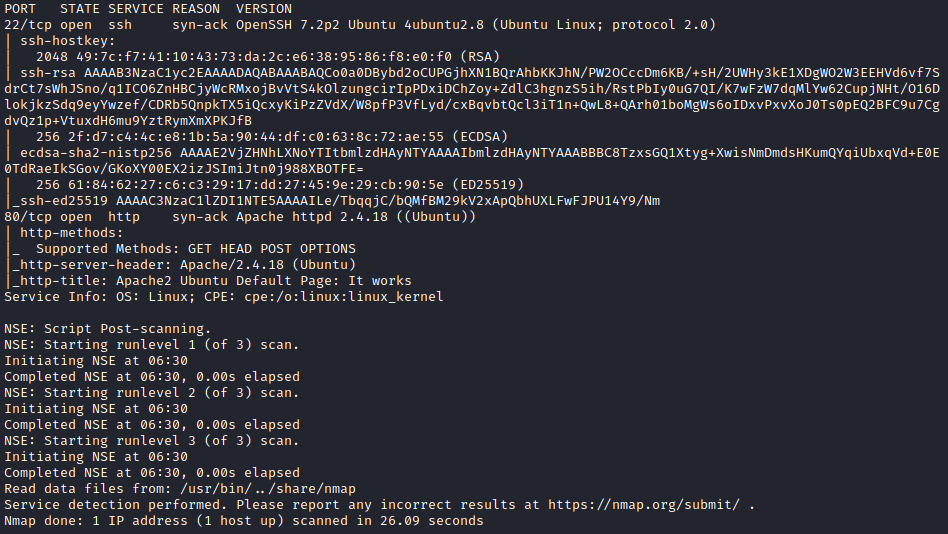
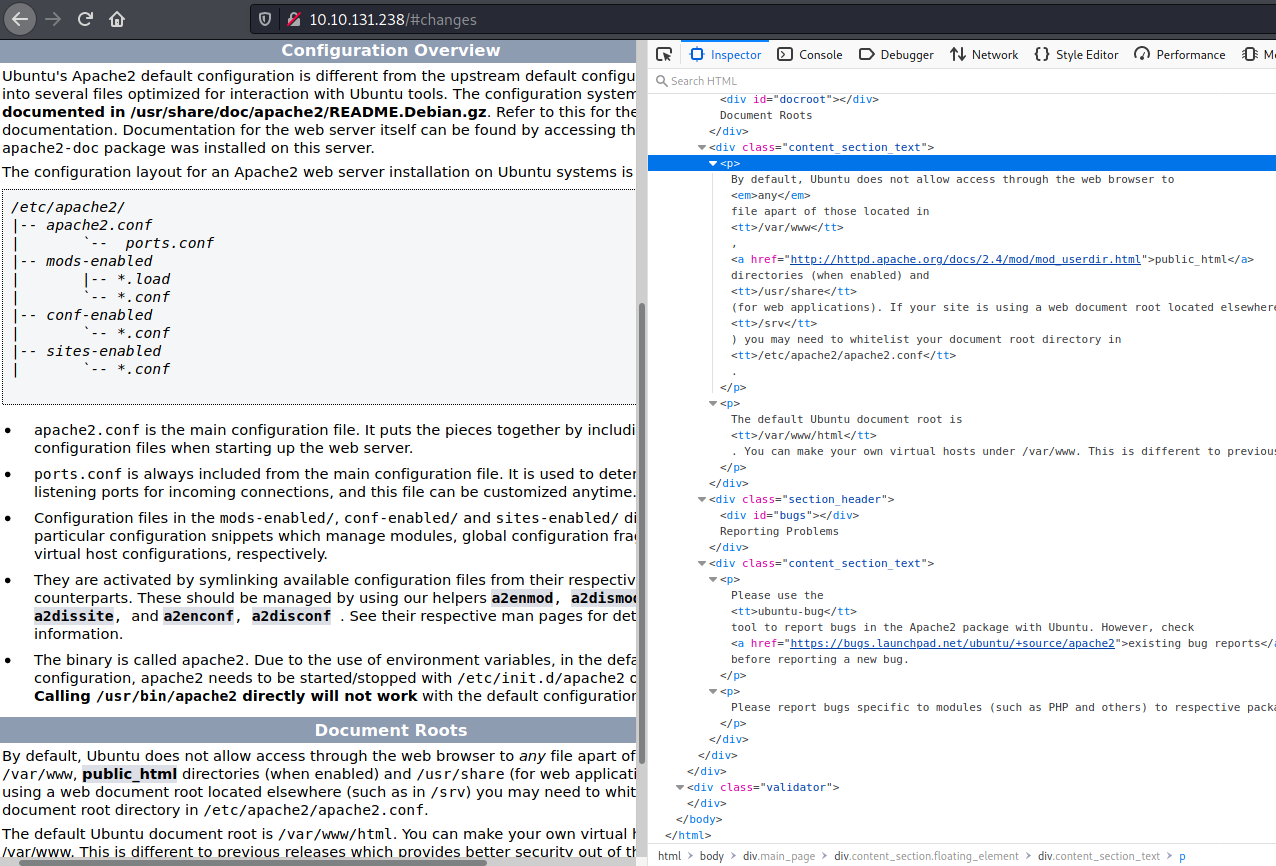
Looks like we have a webserver to investigate but as with many of these challenges we get presented with (initially) the default apache page:
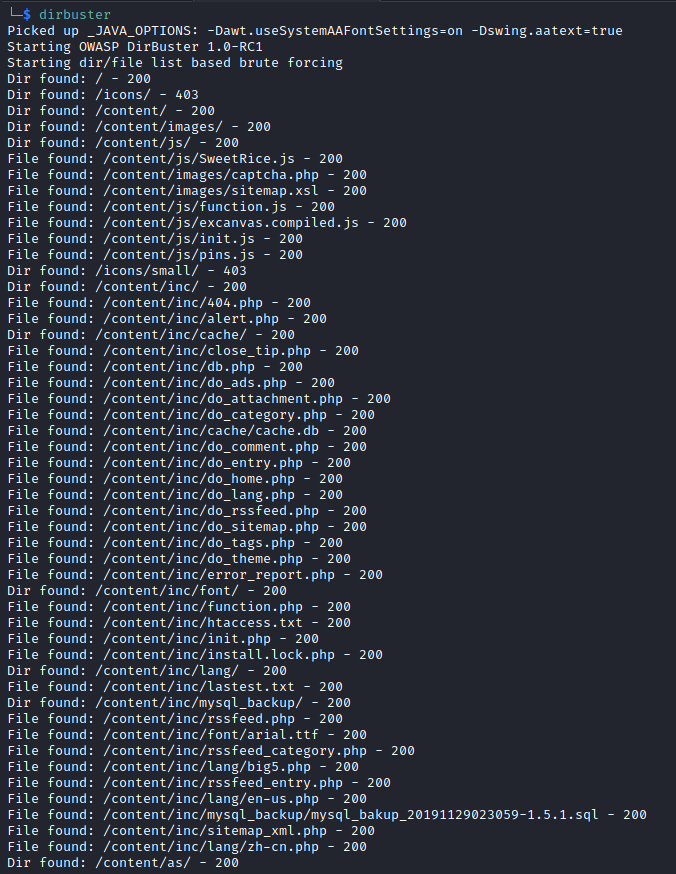
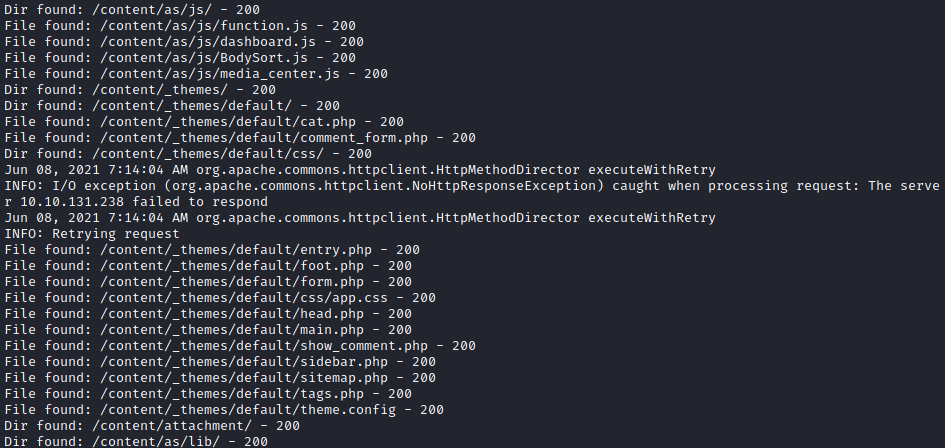
With this overwhelming level of blandness I figured there must be a hidden directory somewhere ... So I let dirbuster run for a long time with the /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt - this gave me pretty much everything I needed to compromise the machine.