`TryHackMe` Linux Fundamentals 3
TryHackMe Linux Fundamentals 3
I'm starting here because the first two rooms are sufficiently explained and they can be easily followed through with; one thing I will note however is that there was a nice tip for checking the file extensions with file -b <filename> - that was quite handy and hadn't seen that before ...
General / Useful Utilities
wgetfor pulling files .wget https://assets.tryhackme.com/additional/linux-fundamentals/part3/myfile.txtscpfor transferring files usingssh. It is bidirectional , meaning we could download and upload from either machine.;; to send a file to a remote machine scp important.txt ubuntu@192.168.1.30:/home/ubuntu/transferred.txt ;; to download a file from a remote machine scp ubuntu@192.168.1.30:/home/ubuntu/documents.txt notes.txt- For hosting files quickly we can use the
http.servermodule that comes withPython3.mkdir flag mv .flag.txt flag cd flag; python3 -m http.server 80 ;; now to pull the file from localhost wget http://127.0.0.1:8000/.flag.txt
Managing Processes
There could be a whole book on just the way in which Linux handles processes, how processes are created and managed by the operating system - but for this exercise we're just going to look at the tools which help us understand how they work, how to navigate the process table and the concept of "scope".
When we type ps with no arguments, we get all the processes for the scope of this particular session:
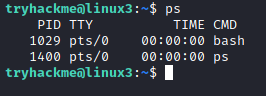
All we have in this session is the bash shell and the ps command we just entered. Call it again and we see the PID has been incremented.
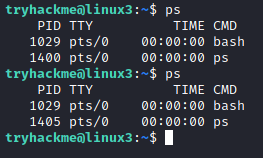
You can see that four other processes had finished by the time I called it again , but the increment is linear... To see the activity of all terminals and shells of the user we can provide the a option
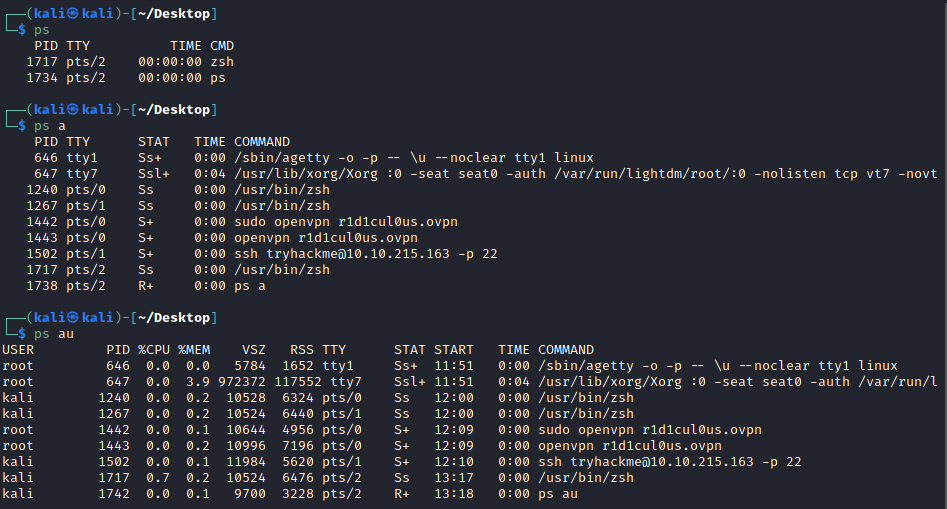
ps a shows all of my activity from all shells and the ps au just formats it into a human readable style.
If we included ps aux then we include every process that has ran since the computer started up - which is a lot of processes:
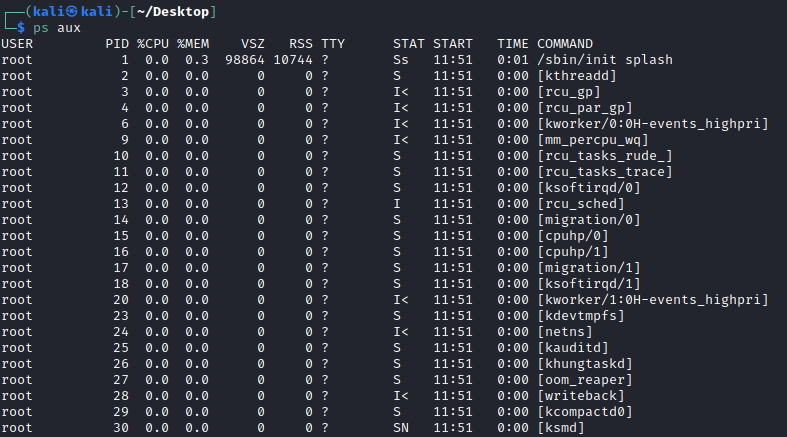
Some of these processes might still be running, as many of them are daemons , system services etc. To see all running processes on the computer, we can use top.
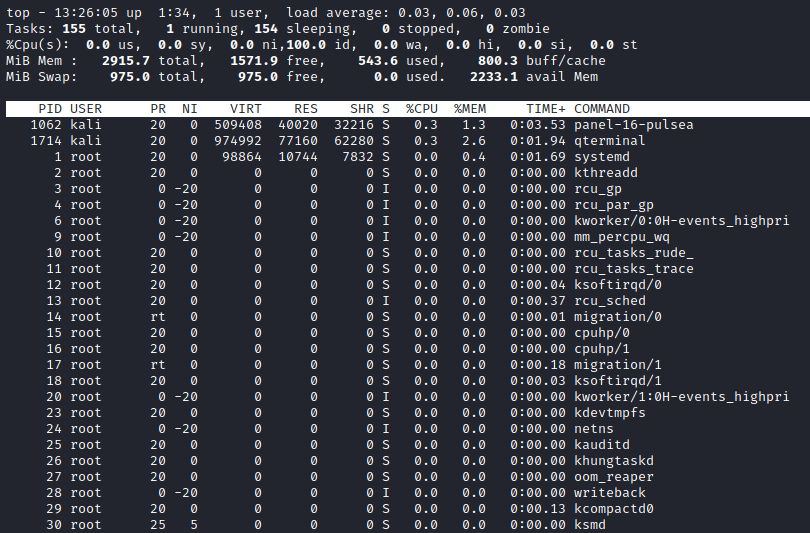
We can seen that many of those services from above and still going .
Managing Processes
You can send signals that terminate processes; there are a variety of types of signals that correlate to exactly how "cleanly" the process is dealt with by the kernel. To kill a command, we can use the appropriately named kill command and the associated PID that we wish to kill. i.e., to kill PID 1337, we'd use kill 1337.
Below are some of the signals that we can send to a process when it is killed:
SIGTERM- Kill the process, but allow it to do some cleanup tasks beforehandSIGKILL- Kill the process - doesn't do any cleanup after the factSIGSTOP- Stop/suspend a process
How do processes start ?
The kernel is the very first process to be launched by the bootloader , which runs in kernel space and establishes a demarcation of kernel addresses - outside that , everything is "user space". For the user to write to. For Linux systems, the transference from kernel to user space is done with systemd . It is the first process that gets started in user space and by which all other processes are a descendent of. Moreover it has a PID of 0. All children get added onto the CPU stack with the fork() function which copies the general scaffolding of the systemd process, cleans it off all specific configuration data and allows the space to be used for this job.
Whilst all processes are children of systemd they shouldn't all be allowed access to each other, as this can cause security issues, overwrites and other consequences. We need to encapsulate processes into a fixed set of resources (only the functions and the system resources that they need) and nothing else. This is where the concept of namespacing comes in - and why employing this methods keeps Linux somewhat secure. The idea is to replicate the interfaces to system interfaces for each process so as to make it easier to keep track of each process and to quickly stop it from making attempts outside of these interfaces. This is exactly what Docker does - just automated all for us.
systemctl is the command line interface for systemd functions and we can choose to start and stop services like apache2 if we wanted a webserver running. We could do systemctl enable apache2 if you wanted this service to run automatically on startup ... I use this for things like Bluetooth though.
Speaking of webservers, they must use some form of namespacing if they are to be considered secure - as this would protect against hackers being able to roam around the wider system if they even managed to all the work it takes to break in.
Pushing process to the background
If we don't want to wait for the command to return to our terminal and proceed with work we can append the & operator which will push the job into the background during its execution. If we have something like a script which is being executed in our terminal and we can't append an & , then we can hit CTRL-Z instead and this does the same thing. To bring the process back into view we can type fg.
Resources
- https://www.toptal.com/linux/separation-anxiety-isolating-your-system-with-linux-namespaces
Automating jobs with cron
It's a pretty simple system that has been going for decades now , where the cron process is a daemon which looks for jobs , called crontabs which are kept in /var/spool/cron/crontabs . We edit this to add jobs (a single tab) using this format:
;; minute hour day-of-month day-of-week month-of-year command
0 12 * * * echo "this ran"
So this will run on the 12th hour , without a minute to spare , every day of every week in every month.
This can be confusing to begin with, which is why there are some great resources such as the online "Crontab Generator" that allows you to use a friendly application to generate your formatting for you! As well as the site "Cron Guru"!
Package Management
I will be talking about Ubuntu for the most part here, but the principles are the same for all Linux distributions.
When developers wish to submit their software to the community they will submit it to an apt repository. If approved, their programs and tools will be released into the wild. Two of the most redeeming features of Linux shine to light here: User accessibility and the merit of open source tools.
When we want to update our computer, Ubuntu goes into /etc/apt/sources.list which keeps a record of all the online repositories that are deemed trustworthy:
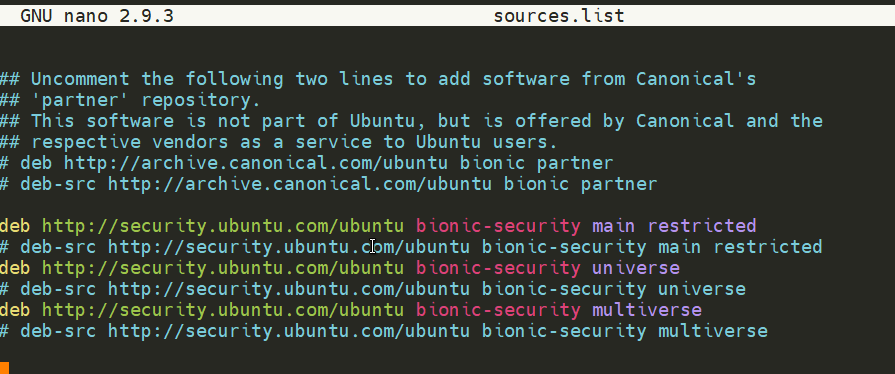
Whilst Operating System vendors will maintain their own repositories, you can also add community repositories to your list! This allows you to extend the capabilities of your OS. Additional repositories can be added by using the add-apt-repositorycommand or by listing another provider! For example, some vendors will have a repository that is closer to their geographical location.
Adding a repository
If we wanted to download something like Sublime text editor, which isn't in the default repositories then we have to do two things:
- To preserve the integrity of our system and maintain a high level of security, we need to get the GPG Key from the software vendor - as this identifies them and allows us to trust in the software. Without it, anyone can masquerade as the vendor. We can go to the website and download the
tarpackage, but this extra step reduces potential malware to near 0. - After that we add the repository URL into our custom sources file , for this example
sublime.listin/etc/apt/sources.list.d/.
We can download the key by doing:
wget -qO - https://download.sublimetext.com/sublimehq-pub.gpg | sudo apt-key add -
And then we make the sublime.list file and add :
deb https://download.sublimetext.com apt/stable/
After we have added this entry, we need to update apt to recognise this new entry – this is done using the apt update command . Once successfully updated, we can now proceed to install the software that we have trusted and added to apt using apt install sublime-text
Removing packages is as easy as reversing. This process is done by using the add-apt-repository --remove ppa:PPA_Name/ppa command or by manually deleting the file that we previously fulfilled. Once removed, we can just use apt remove [software-name-here] i.e. apt remove sublime-text