Introductory Networking
Introductory Networking
In this guide I shall be going over some of the topics covered in the Tryhackme room Introductory Networking, with a few other bits and pieces so as to keep in line with the CompTIA Pentest+ exam. Added extras being hping , wireshark
Categorisation : The OSI model and the TCP/IP model
Nowadays children are taught the meaning of the TCP/IP model, which is fine but I like the fact that we can go into more granular details about what constitutes certain technologies, frameworks and necessary layers. It's all about protocols and standards though, all the way down. That we shall learn everything above the physical layer - which is the first , being all the hardware (switches, routers, bridges, computers etc) - is just data and representing data in a way in which other computers and humans can understand.
This may seem odd , but I want to go from top to bottom, so given these are the layers:
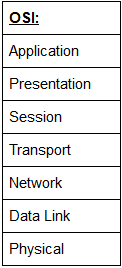
I'll be starting at the application layer and going down to the hardware.
The Application Layer is one which essentially has all the luxuries, formats and systems already defined for it to run across the internet so the application is just a protocol which can specify more higher-level instructions - like HTTP or FTP and they are descriptive purely within the realm of their domain , they don't need to know how the packets get to the client/server, they don't care for the architecture or the IP addresses, they can talk the language of data. Programs and applications can use the application layer if they want a certain type of application data , whether it would be files from a file server or some HTML pages from a website.
Now the application layer does have some standards to uphold if it wants to be able to speak in the pure language of wants and needs, it will need to defer some of the syntactical structures to the presentation layer, which is all about how data should be formatted , so it is secure, structured and optimised (think whitespace optimisation for files, compression for images). Even though these two computers may wish to speak the pure language of data when that request goes over the wire, it may not always be the case that packets can be understood , due to differences in operating system, their version etc. So things like the presentation layer are the first step to unifying these.
Next is the session layer. Which would take this packet that is going to the client, now that it is all nice and formatted and will seek to build a connection with the client computer. The session layer is a pretty thin veil over the actual transportation of the packet , the session layer doesn't have the skills to traverse packets over the wire just yet, but what it does do is take all these structured requests/responses are categorises them, keeps track and maintains the requests/responses of each application separately , and then all the messages for that app. This means we don't have any problems when we open our browser (application) , and open many tabs, as these will all now be sessions within that application. Without the session layer categorising connections and keeping track of whether they are open, closed etc would make it very hard to do multi-tasking operations over the internet.
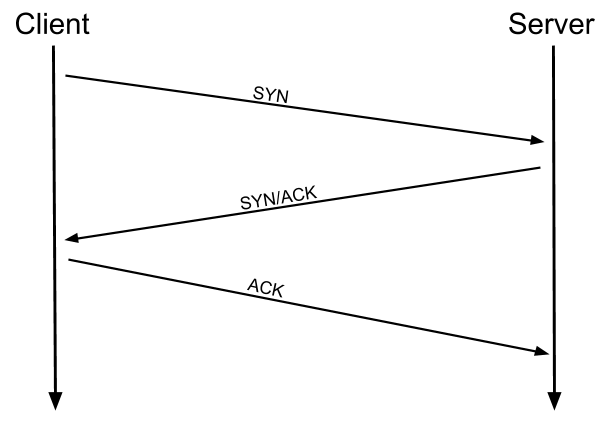
So , the session relies on some framework which can tell the session layer whether two systems have connected, what their status is and that makes it easier to keep a more accurate session table. The layer which is in charge of transporting packets and establishing connections is the transport layer. This is where we see Transmission Control Protocol/User Datagram Protocol (UDP) in action, though these two differ significantly in philosophy. TCP is all about establishing a relationship with the client, that we know of their status, whether they got our packets, sending the packets in order. Being a connection-based protocol it is a lot more reliable, and for files that are sensitive , quite chunky we want to make sure it is sent over securely , and in the knowledge that if the packet corrupts or they get there all jumbled up the client can request again. UDP is an entirely different beast, and it is a connectionless protocol , it will just send packets to the client and they will arrive in whatever order they happen to come in , there is no guarantee they will even get there as no connection is really established beyond the initial request of displaying interest. As mentioned earlier, TCP is a connection-based protocol. In other words, before you send any data via TCP, you must first form a stable connection between the two computers. The process of forming this connection is called the three-way handshake.
When you attempt to make a connection, your computer first sends a special request to the remote server indicating that it wants to initialise a connection. This request contains something called a SYN (short for synchronise) bit, which essentially makes first contact in starting the connection process. The server will then respond with a packet containing the SYN bit, as well as another "acknowledgement" bit, called ACK. Finally, your computer will send a packet that contains the ACK bit by itself, confirming that the connection has been setup successfully. With the three-way handshake successfully completed, data can be reliably transmitted between the two computers. Any data that is lost or corrupted on transmission is re-sent, thus leading to a connection which appears to be lossless.
Now, it is assumed that the client knows the address of the recipient, otherwise we would be sending them to goodness knows who, but this address which is the network layer address that represents a user is called an Internet Protocol (IP) address. It works in the same a regular address does, say for example:
42 Somewhere Avenue , Random Road , Maryland , USA.
;; we have increasingly more general levels, of which someone can narrow down our addr.
;; IP does the same
10.10.68.70
;; we often see an address of this style on Tryhackme boxes, the 10.10.*.*
;; being the demarcation for the network portion of the address,
;; and the subsequent address being the client portion.
Formally speaking this is called IP subnetting, where we allocate a portion of the address to represent the ownership of the business, network etc - or we could do both - having the first octet representing the company, then the second octet representing the department etc. But this isn't always practical or necessary. The level of subnetting used by Tryhackme rooms is called Class B subnetting as we allocate two portions "worth" of the address to the network and not to the actual computer. You can have what's called Class D , but this is where we don't care about the individual host then, and so we are multicasting , sending data to multiple hosts that are on that network. Addresses like the 0.0.0.0 can be used as a generic IP address on the host , for jobs like setting up a server etc.
I want us to jump from the internet down to the local network now , where IP addresses still apply but we orient ourselves now to a much smaller base, where we know everyone and the network is theoretically cut off from the outside world - without a router of course. The standard private network relies on a router for communicating with outside servers, and routers will manage our requests for us - in fact the router will use its IP address, which is public to the world - rather than our private IP address which the router would use to send messages internally. Thus there is this notion of public and private IPs, with public ones having a finite number of accepted values, as IP (version 4) addresses were given a 32-bit space. 4 octets (eight bit sections):
Moreover there are only a finite total number, around 4.3 billion and when those public IPs are all taken by registered corporations, routers etc then we need something else! Which is where IPv6 came in, which has a 128-bit total address space - so instead of 232 , it's 2128 which is 340 trillion trillion trillion IP addresses...
At this stage we're working with what is referred to as Logical addressing (i.e. IP addresses) which are still software controlled. Logical addresses are used to provide order to networks, categorising them and allowing us to properly sort them. Currently the most common form of logical addressing is the IPV4 format, but as we shall see in the coming years it'll be a lot more IPv6 on the public side. In terms of home networks, we are free to stick with simple IPv4 - the router does the job of translating them.
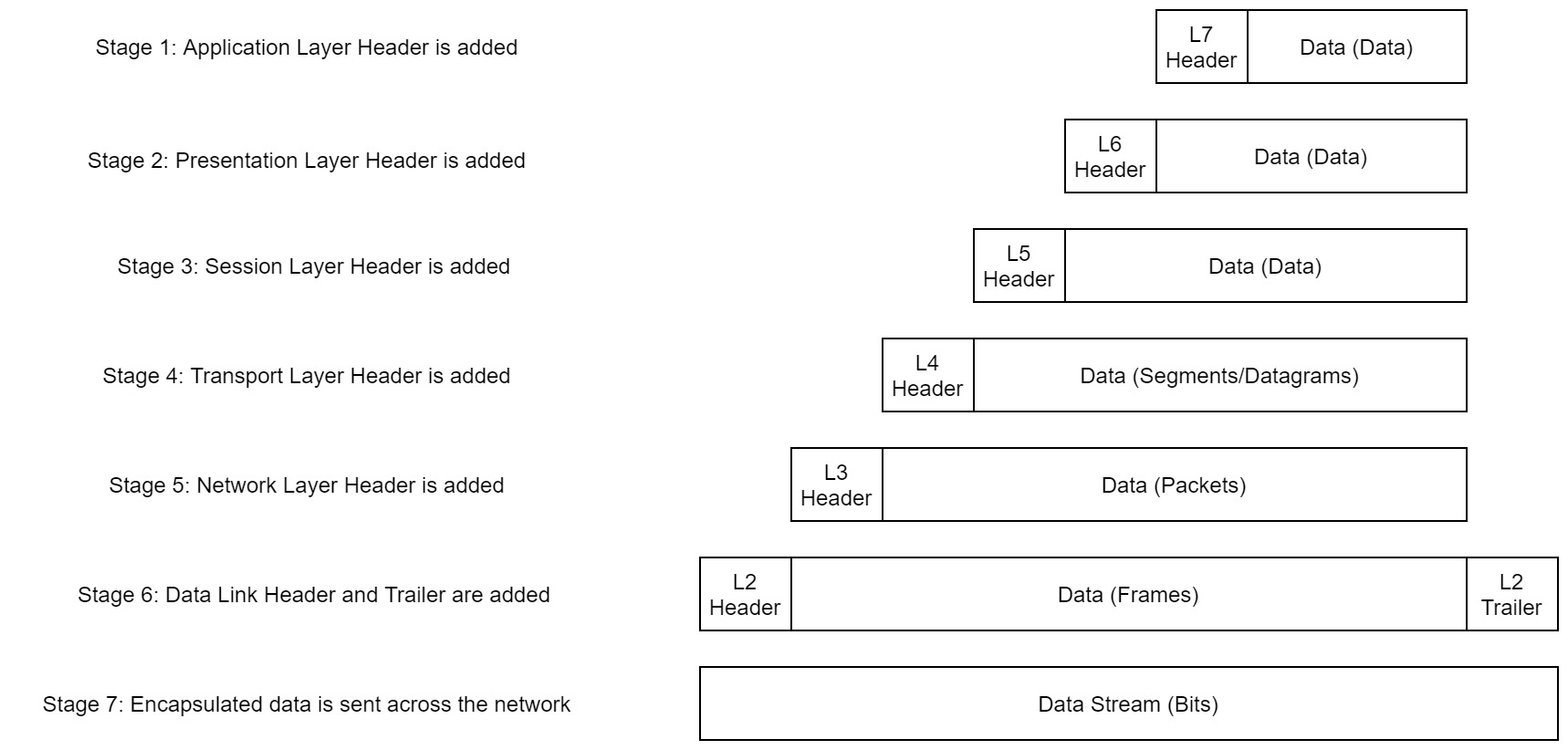
As we drop another layer , to the data link we see go from global networking to local networking - and this usually refers to the use of hubs, switches, Ethernet etc. Routers can be used to do local and global networking operations , but this layer is more to do with all the networking that goes on within a department, which uses hardware addresses - the ones on our Network Interface Cards which a Media Access Control (MAC) address burned into the card itself. This identifies the computer on local networks, and when these computer send packets, this frame (layer two packet essentially) is included and then other layers their packets around the last layer. This is called encapsulation.
Layer two is special because it includes a trailer with the packet, allowing the client to see whether or not the packet has changed somewhat during transmission , as the client performs a calculation on the packet to illustrate the bit size etc. If the packet is modified, the calculation gives another value, and hence there has to be a resend. A router would send a switch a packet , and then the switch would check whether the destination IP address is included in the ARP table, otherwise it's dropped. Address Resolution Protocol maps an IP address to its MAC for all devices in the local network, so we can then determine the right client. The MAC addresses are matched to a given port, and hence the bits go down the right wire.
The last layer then is the physical , which makes all this possible. The wires, machines, computers etc.
Encapsulation
I mentioned this briefly earlier on , but this is where packets slowly compose of more and more packets when its being sent to the recipient, who goes through the process of breaking it down.
Layer two provides some protection, but encapsulation is just a nice and efficient way of sending all the right protocol data over the wire without added complexity.
General Networking Tools
This is where we become more exam oriented and look at the different tools at our disposal for sending packets, crafting packets and inspecting them etc.
The simplest of the networking suite is arguably ping, which is used to identify whether a host can issue packets to a domain like google.com and whether that host is capable of receiving ICMP packets (either the host is down or firewalled). Internet Control Message Protocol is basically a method of checking the status of networked devices - used in debugging really.
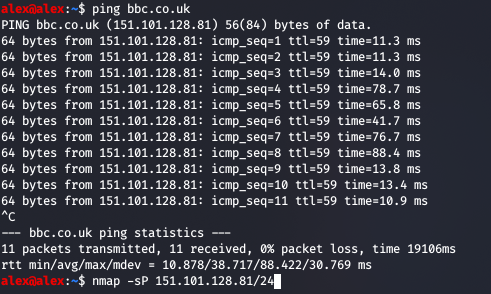
Now I'm not going to run that last command as that is quite loud and intrusive, but the ordinary ping is harmless enough and as it first performs a DNS request we get to see the IP address of the host which is pretty nice.
Next up is traceroute which can essentially show us the journey of packets to their destination.
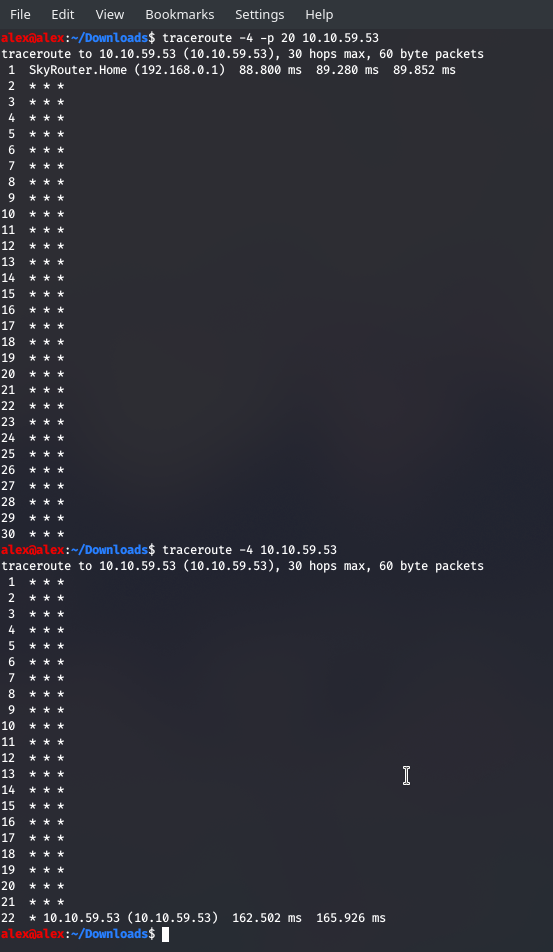
So we built up a bit more information about the client up to this point - we could attain their IP through DNS, their proxies / DMZ through traceroute and now we can use WHOIS to see more about all the registered domains, records, email servers etc.
It's quite a hefty report for the bigger companies, especially the tech companies - but don't worry about raising alarms with this, you're reading off of the DNS databases not in reach of the corporate touch , and you only need to send a few requests to get everything you need.
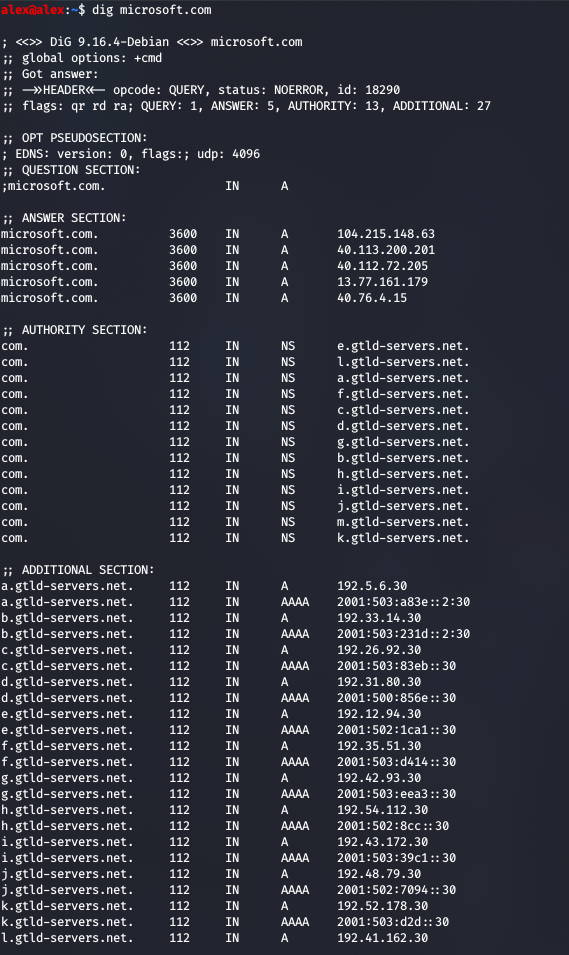
A newer tool for doing DNS stuff is dig. This tool is straight to the point, well designed and the output is clean:
Crafting packets
We want to be able to craft our own packets in order to modify existing packets we've captured, to fragment packets in odd ways, to assemble packets from scratch etc. One tool which is quick and dirty is the hping tool:
hping3 -S -V targetsite.com -p 8080
;; hping3 is the latest version, and it looks like a pretty powerful tool ! This command
;; sends a TCP SYN packet, with the V for verbose to port 8080...
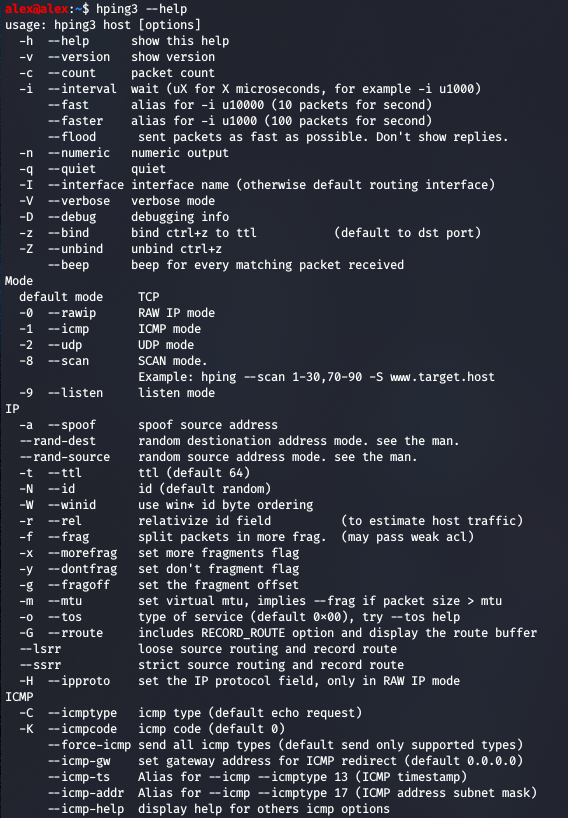
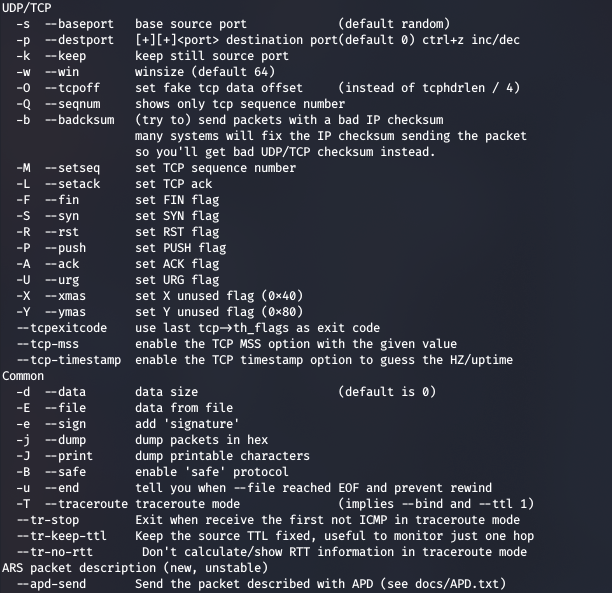
So we can set signatures on packets, in case we find a particular key, we can gather payloads from files using E - in the case of a replay attack possibly...