Introduction to John the ripper
Introduction to John the ripper
- John is a password cracker
- Supply a wordlist, where John will take each input , hash the word and then check whether the hashes are the same. This works as the algorithm is the same on the attacker's box, the victim's box etc. But is it a good idea to have unique implementations in every situation. This is where Hash-based Message Authentication Code (HMAC) which is basically where a client would use a unique key on their message first and then hash to make it more resistant to attack.
Automatic Cracking
John has built-in features to detect what type of hash it's being given, and to select appropriate rules and formats to crack it for you, this isn't always the best idea as it can be unreliable- but if you can't identify what hash type you're working with and just want to try cracking it, it can be a good option! To do this we use the following syntax:
john --wordlist=[path to wordlist] [path to file]
--wordlist= - Specifies using wordlist mode, reading from the file that you supply in the following path...
[path to wordlist] - The path to the wordlist you're using, as described in the previous task.
Example Usage:
john --wordlist=/usr/share/wordlists/rockyou.txt hash_to_crack.txt
Identifying hashes
In case John can't recognise the hash format, we can use the

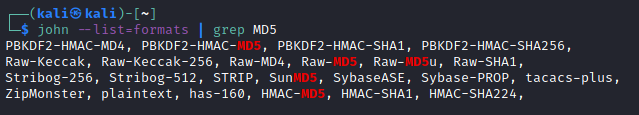
Kali comes with hash-identifier to help us out find the format, which we can then supply to John. There aren't any bells and whistles on this implementation so we'll go for Raw-MD5.
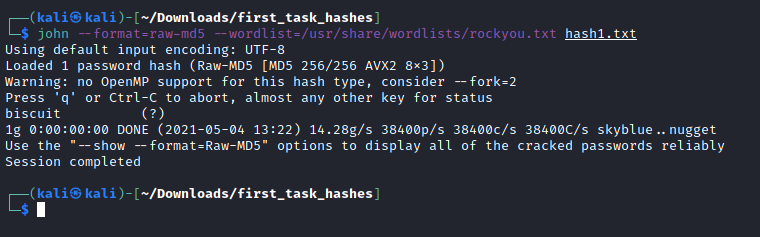
Then we do the same for each hash...
;; hash-identifier , copy in each hash
;; list john formats for the hash
;; john --format=[format] --wordlist=[rockyou.txt] hashN.txt
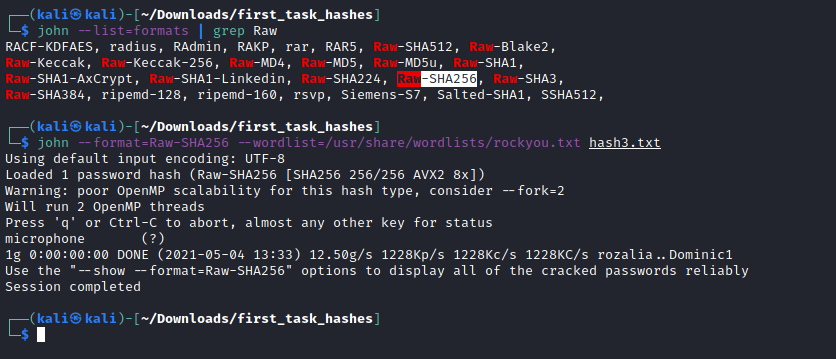
The last hash isn't the first option , so try Whirlpool ...
Cracking Windows Authentication Hashes
User accounts on the Windows Operating System are hashed to stop them being read so easily, using the NTLM hashing algorithm. NT originally meant New Technology , as the term was shipped as Windows-NT to signify the moving away from DOS, but this whilst this term has been dropped on the OS name technologies such as these have NTLM included...
You can acquire NTLM hashes by dumping the SAM database on a Windows machine, by using a tool like Mimikatz or from the Active Directory database: NTDS.dit. You may not have to crack the hash to continue privilege escalation- as you can often conduct a "pass the hash" attack instead, but sometimes hash cracking is a viable option if there is a weak password policy.
The reason they're called Authentication hashes, is because they are the hashes which LSASS, SAM reference during the logging in process. Some services allow us to pass the hash directly to a service and hence they become even more vital for proper authentication.
Cracking Linux Authentication Hashes
The place where user account password hashes are stored is in /etc/shadow and in this file a password may look like this:
root:$6$2nwjN454g.dv4HN/$m9Z/r2xVfweYVkrr.v5Ft8Ws3/YYksfNwq96UL1FX0OJjY1L6l.DS3KEVsZ9rOVLB/ldTeEL/OIhJZ4GMFMGA0:18576::::::
The first segment is the username, the second segment denoted by $6 specifies the algorithm that Linux has used on this hash - so is it SHA256 or SHA512 ? The different numbers can be seen here.
ID | Method
─────────────────────────────────────────────────────────
1 | MD5
2a | Blowfish (not in mainline glibc; added in some
| Linux distributions)
5 | SHA-256 (since glibc 2.7)
6 | SHA-512 (since glibc 2.7)
For John to crack this hash it needs to know whether or not the account has a salt, and the general format that the account has so it can begin to craft brute-force attempts. There is a tool called unshadow which takes the two sources of information John needs (the relevant /etc/passwd account info and the /etc/shadow entry) and formats it. This allows John to instantly grasp what the algorithm is, the salt (if any) etc.
In our example file we have the two bits of information given to us:
;; from /etc/passwd, which is sometimes publicly readable...
root:x:0:0::/root:/bin/bash
;; from /etc/shadow
root:$6$Ha.d5nGupBm29pYr$yugXSk24ZljLTAZZagtGwpSQhb3F2DOJtnHrvk7HI2ma4GsuioHp8sm3LJiRJpKfIf7lZQ29qgtH17Q/JDpYM/:18576::::::
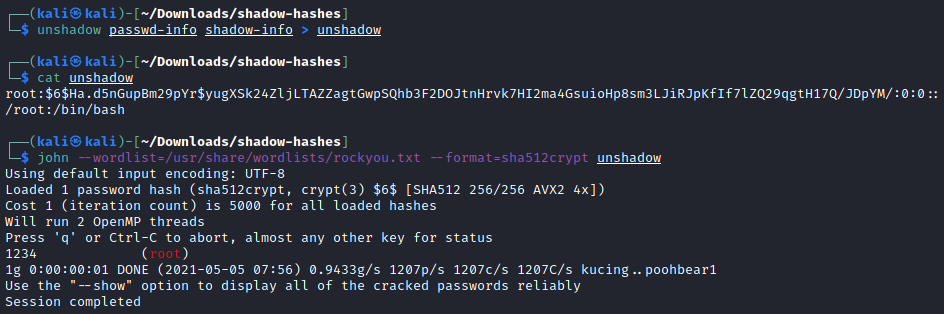
Put these into two separate files and run unshadow
mkdir shadow-hashes; cd shadow-hashes; touch passwd-info; touch shadow-info;
;; then copy the info into the files...
;; now we can format it
unshadow passwd-info shadow-info > unshadow
https://linuxconfig.org/password-cracking-with-john-the-ripper-on-linux
https://samsclass.info/123/proj10/p12-hashcat.htm
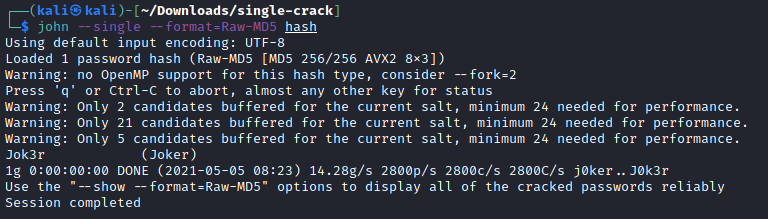
John Single crack mode
The mode we have solely employed to crack hashes has been the wordlist mode, but there are other methods such as the single crack mode. What this means is that we take one bit of information such as a person's username and begin to generate a wordlist based on that username - so for example if we were cracking an employee's Linux password hash and her name as Olivia:
;; john single crack mode can be enabled with --single instead of --wordlist=
;; the O can be replaced 0 for example, the l replaced with 1 and we'd see attempts like
0l1v1a
O1ivia
Olivia123
John has some baked-in rule sets which are patterns that help it generate such passwords. I don't actually use this method for pen-testing but instead for generating wordlists that goes toward a bigger , more complete dictionary. You can see how to do that here.
Much like the section above we need to format the hash for John to understand it. For single crack mode we need to supply the username (the thing we generate off of) and the hash like this:
username:hash
Which employs the same Gecos field notation as standard Linux hashes do.
Custom Rules
What do custom rules allow us to exploit?
Password complexity predictability
What rule would we use to add all capital letters to the end of the word?
Az"[A-Z]"
What flag would we use to call a custom rule called THMRules
-rule=THMRules
Cracking with help from additional formatting tools
We have covered the use of unshadow for help in cracking Linux hashes, but there are also:
- Password protected zip files
- Protected RAR archive files
- SSH Keys
Cryptographic protection seems to be everywhere ! Which is why we need formatters for each of these scenarios. Luckily for us we don't need to write these tools ourselves , we can just get stuck in !
The tool zip2john should come natively with Kali :
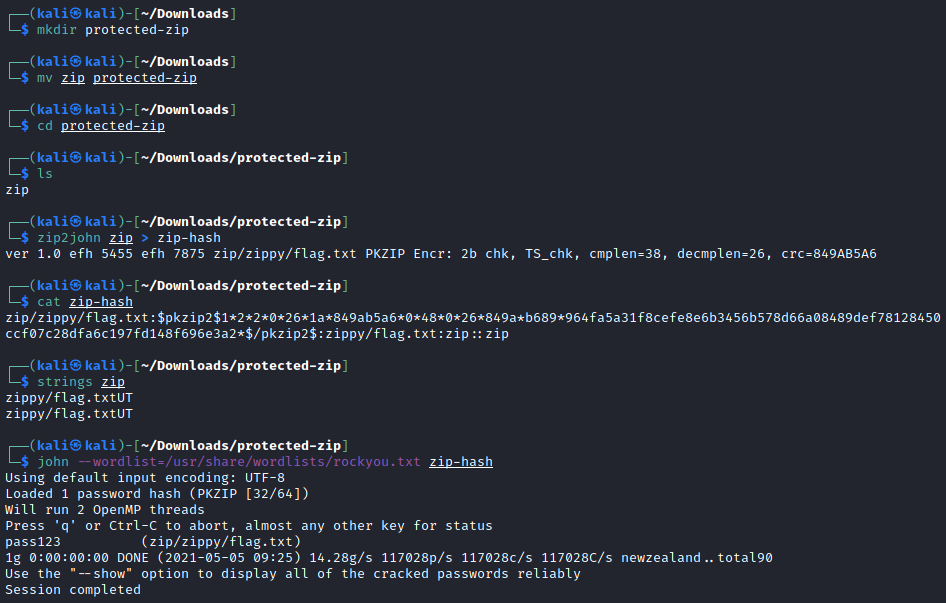
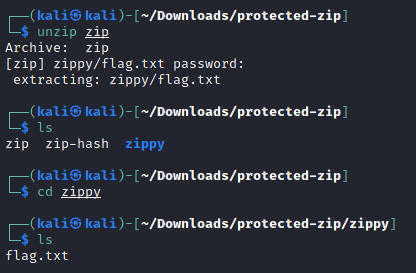
When I typed strings I wanted to see if we could get any file names from the package, and this is the file which has been password protected. Moreover when we try unzip this will be the file that needs authentication. zip2john uses this information to piece together the Gecos field notation that John understands.
Now onto RAR archives.
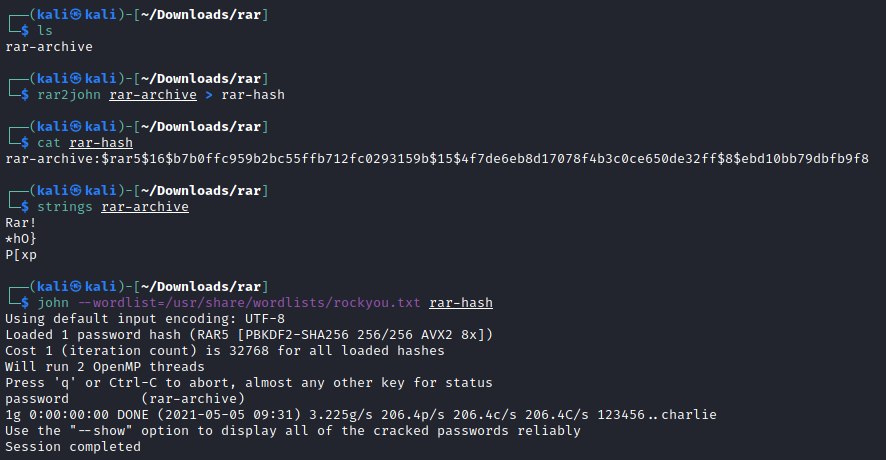
Now engrampa which is the file extractor that I use often times in the GUI didn't like this RAR file and there wasn't a way for it to extract the flag.txt file out ... So what I did was use https://extract.me/ which allows us to supply a password and that got me the file...
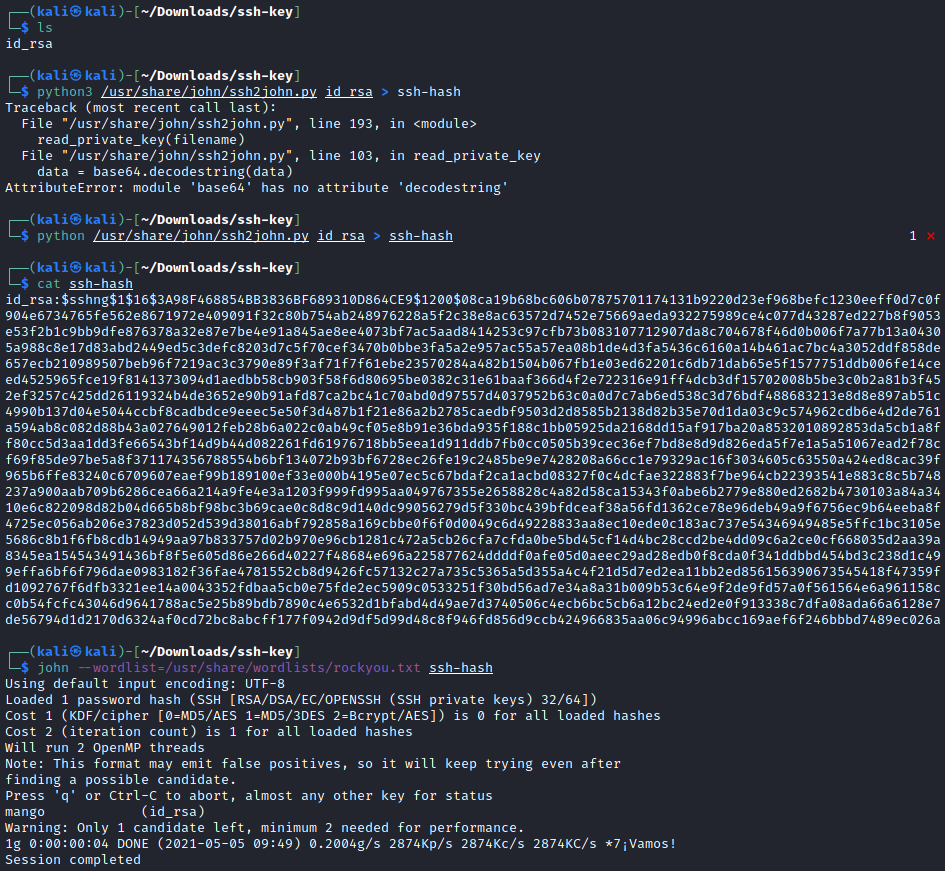
Last but not least, cracking SSH keys with John.
When we have landed on a victim's machine, or we somehow stumbled upon a private SSH key when performing reconnaissance now we need a way to get the password so as to log in. Whilst a key may exist the configuration on their SSH account may only allow a password to be supplied - hence not falling victim to a "pass the key" attack.
We'll use ssh2john , surprise surprise. This can be found in /usr/share/john/ssh2john.py. Keep in mind that python3 seems to stir trouble, so use the python version 2.7.1 ...