Introduction to Windows Host Security
Introduction to Windows Host Security
In this essay I will hope to cover quite a few different aspects of securing your Windows host, and likewise we shall go through some of the exploits that can become utilised in the event of poor security.
The first thing I shall discuss is the simpler case of home systems, and what relatively powerful tools the home user has - say a Parent's laptop which the children might use - and how these tools extend into the corporate environment.
Using Applocker
Windows Applocker is an application that gives administrators the ability to declare rules on certain users in relations to what programs they can or can't execute - based on properties like the file extension (executables like .exe for sure), the file-hash , who signed the program etc. Its sort of like sudoers in Linux.
We can select file paths that the rule should act under, but this also means that for files placed outside of these paths they can evade Applocker rules. More sophisticated rules are in order !
Let's say for the sake of example that this was one of the whitelisted paths
C:\Windows\System32\spool\drivers\color
That means we could open PowerShell up here (unless this has been restricted under the `C:‘ path of course), and download some scripts...
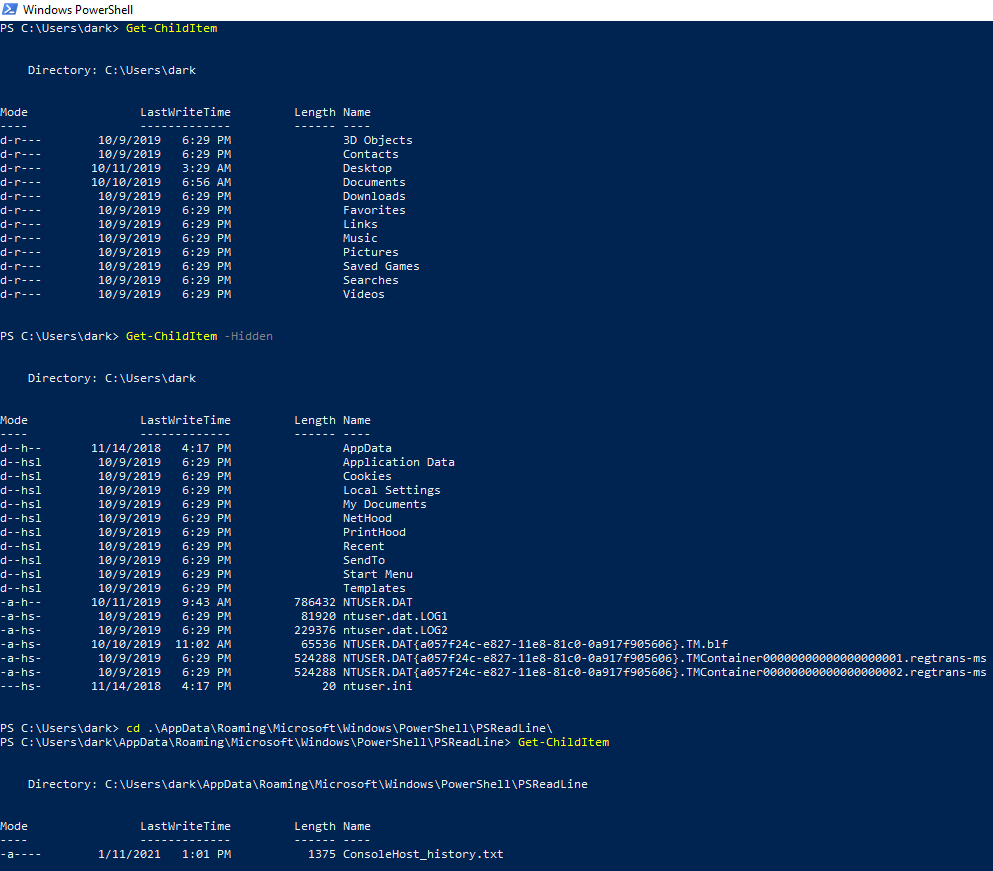
We can also look for the file which keeps the command history of our Powershell sessions (all saved sessions for that matter), and there should be a flag inside !
https://www.aldeid.com/wiki/TryHackMe-Corp
Video on Kerberos : https://youtu.be/LmbP-XD1SC8