Advent of Cyber - Blue Teaming section
Advent of Cyber - Blue Teaming section
This will highlight a combination of skills , such as forensics , operating system functionality etc. The aim is to understand how we can utilise security mechanisms - like hashing - to create a structure of integrity and confidentiality.
Task 21 : [Blue-Teaming] Time for some ELForensics
To start we'll be using the built-in cmdlet Get-FileHash which works quite well for generating a signature for a given file, executable or folder(s).
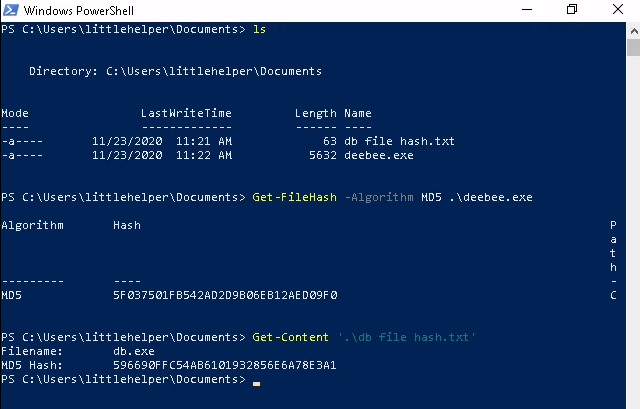
In addition to this we may want to inspect the program itself - for this we can use Strings.exe , which will sift through and find any human-readable information for us.
C:\Tools\strings64.exe -accepteula .\deebee.exe
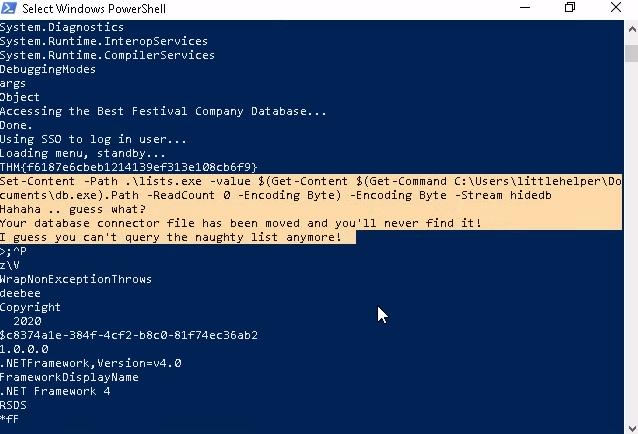
So the Christmas list has been moved ! We need to figure out where it has gone to find out who is in the naughty or nice list ...
Alternate Data Streams
This is a feature specific to the Windows NTFS world, and what it allows us to do is write data to a file, but in different "highway channels", so there can be side-pools of data which a file can hold - now this is most commonly used for malware writing, as a way to hide code from easy introspection , but antivirus programs know of this trick... What we want to do in this box is use the data within one of these streams to identify where the connector has been moved ,as it seems the attacker still wants to link our deebee.exe to it, just outside of our scope of interaction though.
There is a tool called wmic which is the command-line program for the Windows Management Instrumentation , a collection of tools designed to allow an administrator access to the management reports, data and configurations for a given system. You can , with sufficient privileges of course, access the Windows registry and add,remove or re-configure keys and entries. We can use wmic to start and stop processes, run executables - and most importantly here - select the Alternate Data Stream (ADS) hidedb :
wmic process call create $(Resolve-Path deebee.exe:hidedb)
Task 22 : [Blue-teaming] Elf McEager becomes CyberElf
In this task we're going to be looking at another important aspect of forensics : passwords ! Password managers are a good solution to keeping all passwords - within their managed and encrypted table, but this still requires a master key. Do I need another password manager for the password manager password ? This could go on forever... Ideally we would have some sort of biometric or scanner that incorporates with our identity more closely. In this box we shall leverage the fact that the password manager master key is vulnerable and try to accumulate enough data to crack it.
Looking at the folder on the desktop
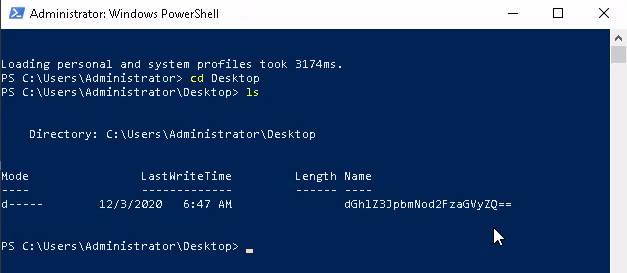
Putting this through cyberchef with the Magic recipe:
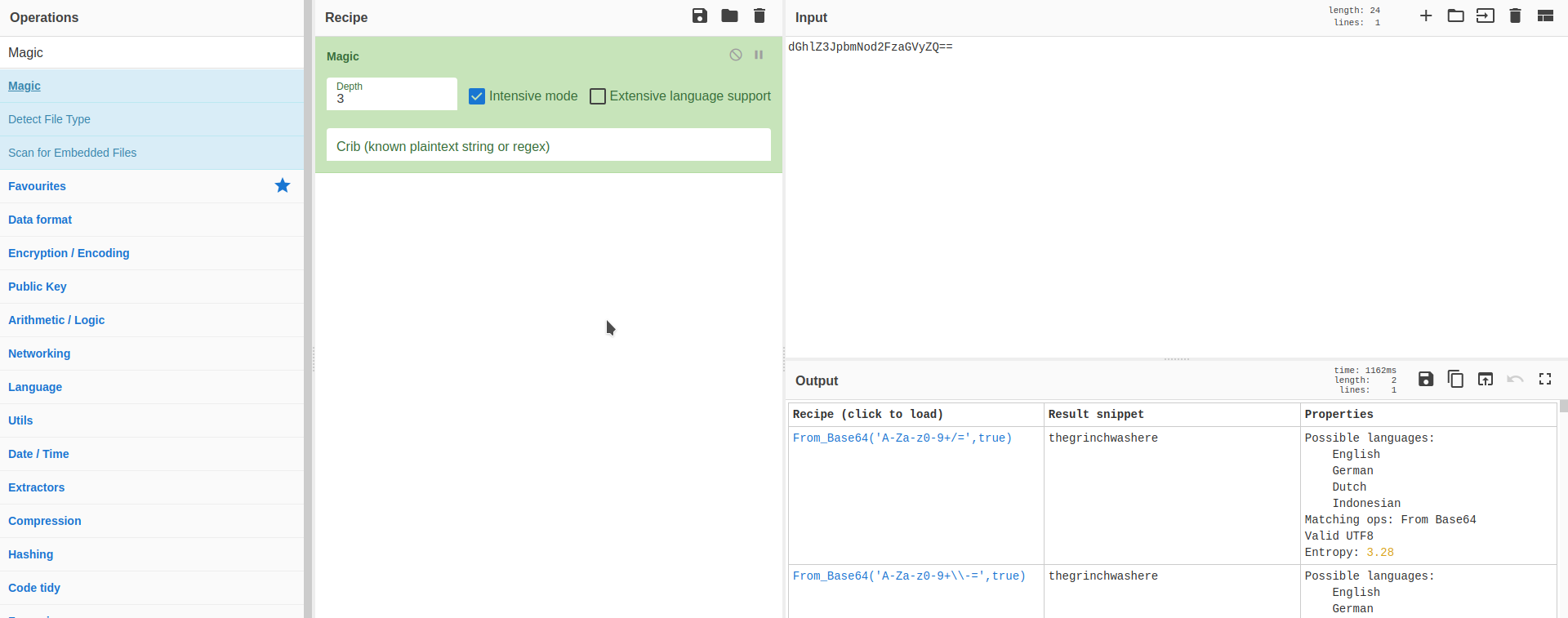
Ah ha! We have data. Now we can log into data and grab the passwords for different things like networking, databases etc.
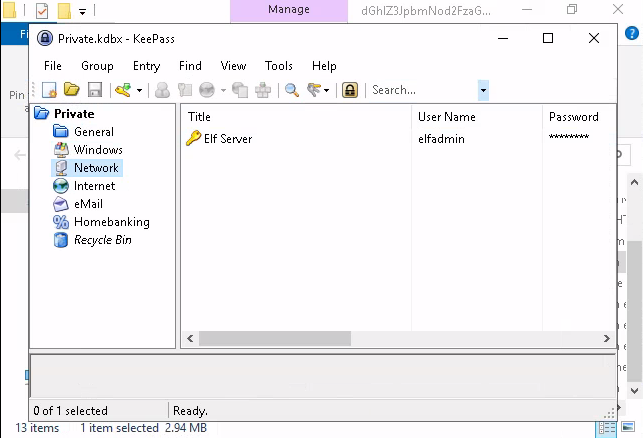
Just double-click and get the respective passwords... The notes that accompany the password for elf server will come in handy for decoding it.
Next is the mail server
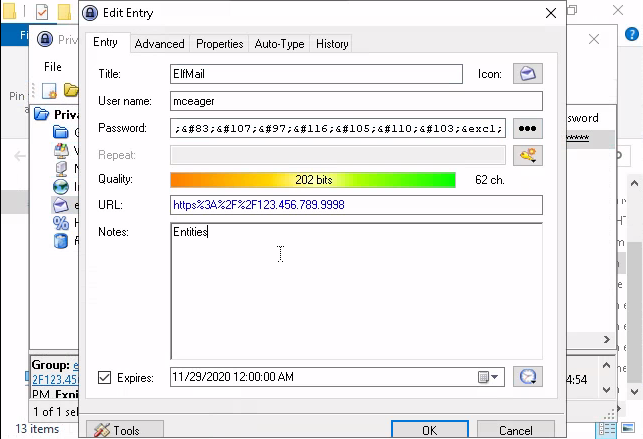
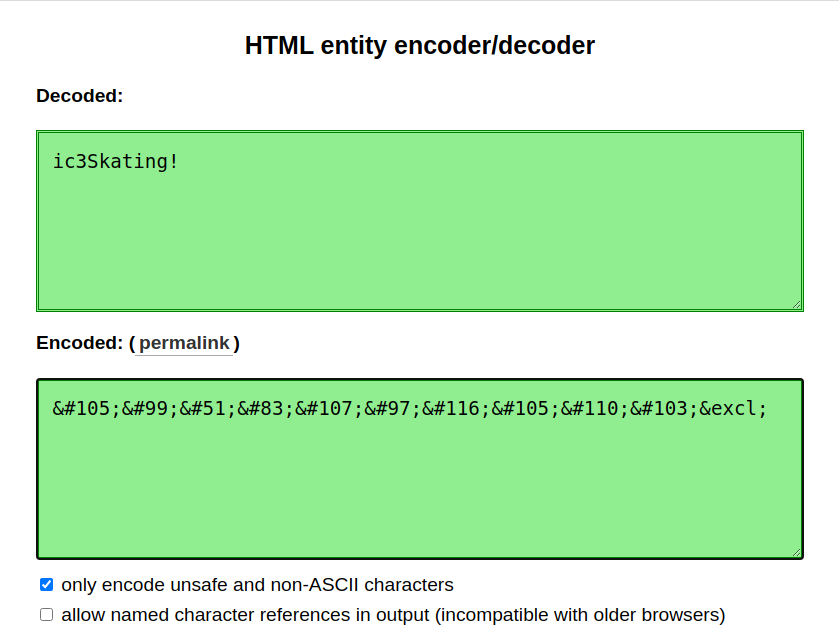
When the note says "Entities" that means we need to look at decoding HTML entities - so we can do:
And now for the last password
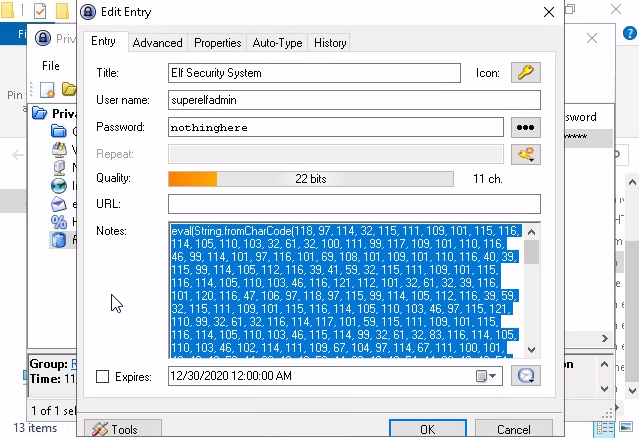
Plugging this into a JavaScript console we get a HTMLScriptElement , and if we start inspecting all the properties:
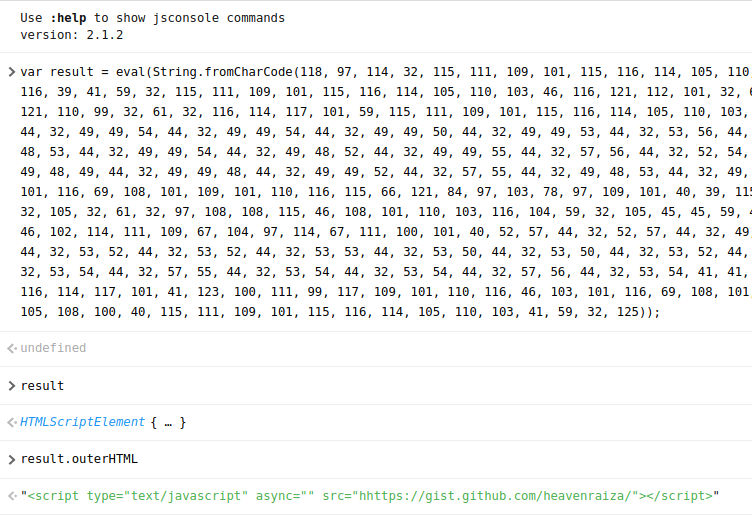
And if you head on there you shall have your answer!
Task 23: [Blue-Teaming] The Grinch strikes again!
In this task we shall be looking at how ransomware can be a potent attack vector, but being that this is a blue team section we want to see how we can defend against this. If you don't have backups, then you're really at the mercy of the malware writer - and if the malware has gone to the trouble of destroying local backups on the system then you will have no chance of reclaiming your data. There needs to be a weekly (ideally daily) backup into a remote site, whether it is the cloud or archived within the offices , so the venom of the malware is lessened.
There are numerous security products that can be implemented in the security stack to catch this type of malware. If ransomware infects an endpoint, depending on the actual malware, there might be a decryptor made available by a security vendor. If not then you must rely on backups in order to restore your machines to the last working state, along with its files. Windows has a built-in feature that can assist with that. The Volume Shadow Copy Service (VSS) coordinates the actions that are required to create a consistent shadow copy (also known as a snapshot or a point-in-time copy) of the data that is to be backed up.
For this to run over and over again - say every week - we would need a scheduler , something which runs to a given timetable - and we can make a process run daily by setting the job to execute every day - in this case - with Windows Task Scheduler. The Task Scheduler enables you to automatically perform routine tasks on a chosen computer. Task Scheduler does this by monitoring whatever criteria you choose (referred to as triggers) and then executing the tasks when those criteria are met (actions).
We can either use the GUI or the PowerShell tools:
Get-Command *Task*
;; will pull task related tools
Get-Process
;; this will give us the table of running processes, with their ids etc.
Now then , onto the task itself.
The first side task is to grab the details of the ransom-note file:
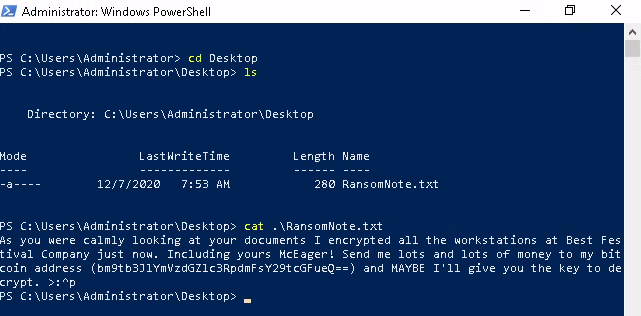
And decoding it
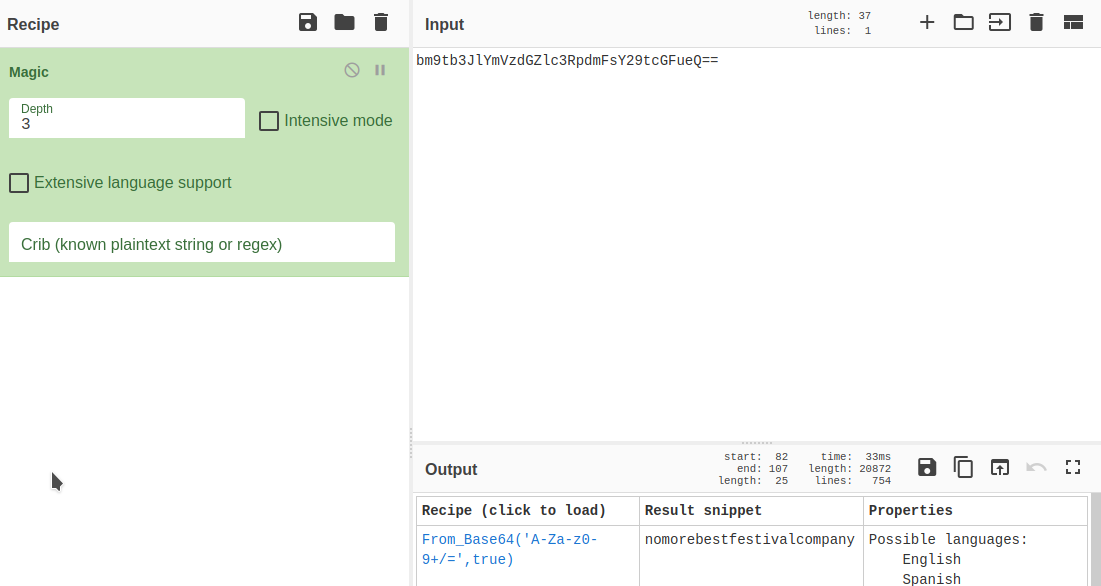
Traditional ransomware will completely encrypt all the files on the system - our only hope are those shadow copies that weren't deleted !
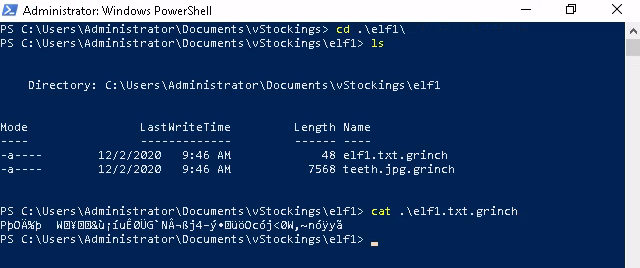
Yep, it seems that the Grinch has done well - it's up to us to figure a way out. Looking back at the Task Scheduler program, we can see a funny looking process:
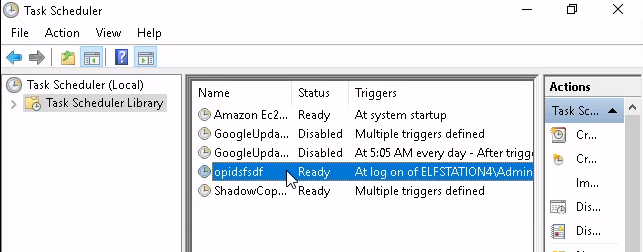
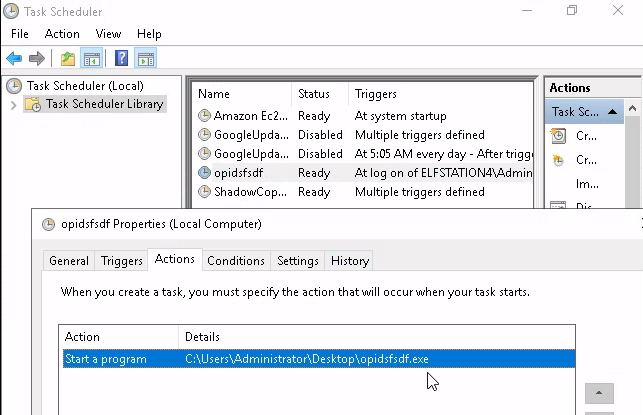
Looking at the triggers and actions it will execute when the user logs on and run opidsfsdf.exe.
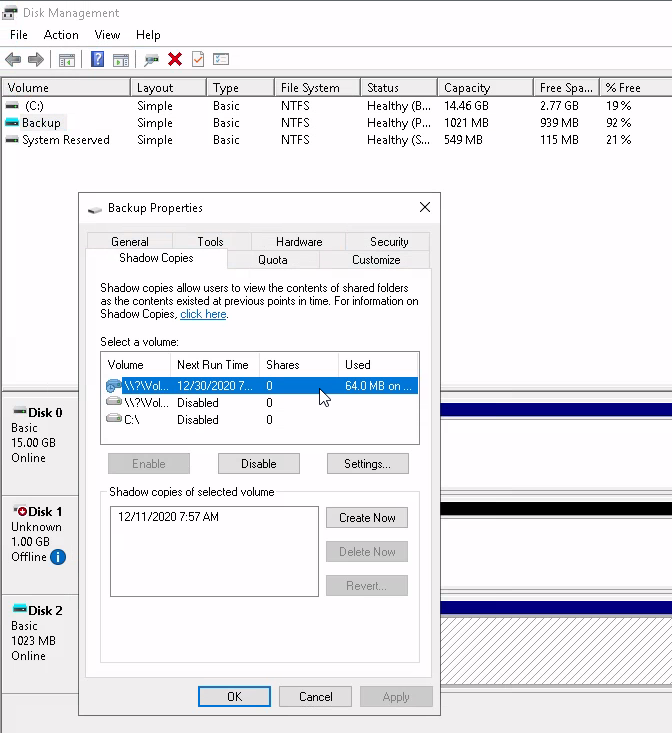
Turning to the Volume Shadow Copy Service (VSS) process now, we can see some of the volume IDs that have been backed up. What we also need to do is check the Disk Management utility to see exactly where these backups are stored - as it's obviously not on `C:‘ , otherwise malware would encrypt it !
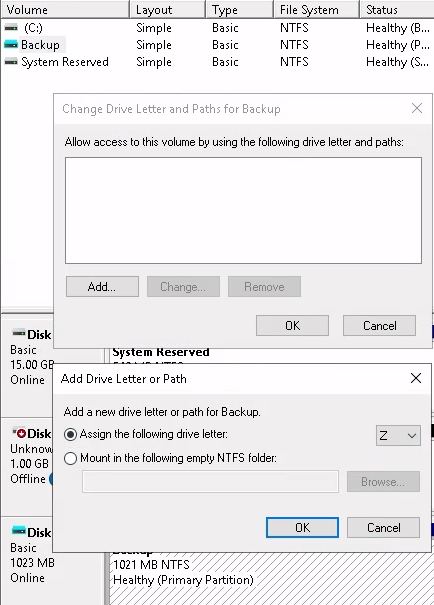
We can see that the C:‘ drive has been backed up as well as some other volumes - but to use any of these we need to mount the volume onto the file system - which we can do by right-clicking and pressing Change Drive Letter and Paths`
It is actually mounted as we see the File System is NTFS , so all we need to do is make it accessible with a drive letter :
And if we look in the Documents Explorer click on View > Details in the top bar and tick Hidden Items
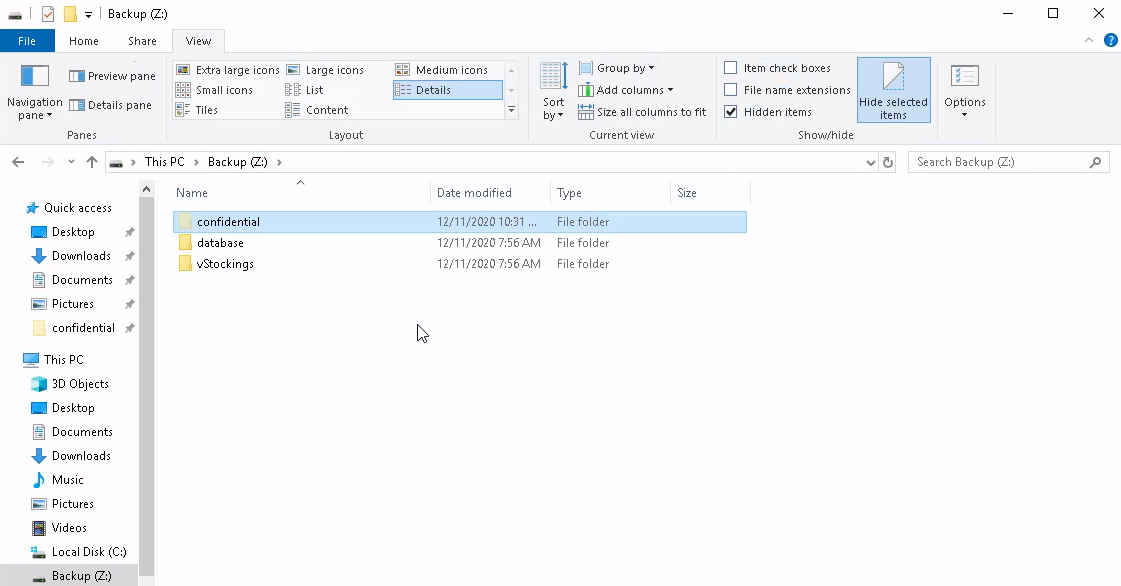
The backup folder holds shadow copies, so these aren't the only versions of the files that we have to look at, moreover we can restore the folder to different versions :
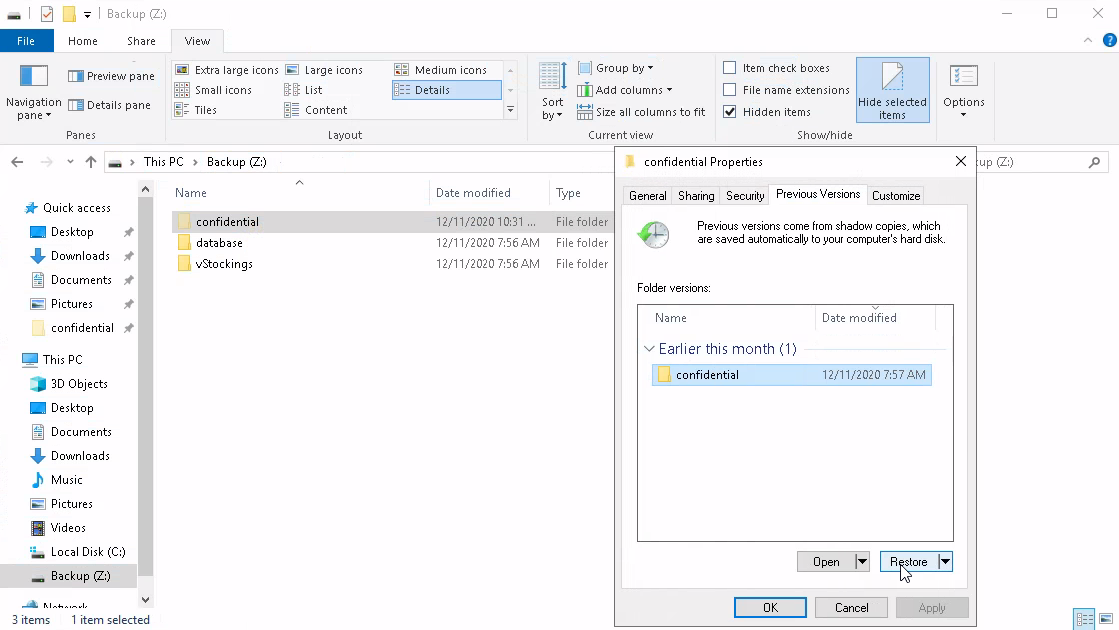
Go into the folder now and we can access the file which holds the flag.