TryHackMe : Introduction to malware
TryHackMe : Introduction to malware
This will be a series, yet again encompassing a plethora of like-minded tryhackme boxes for the purposes of boosting our malware skills ! This will encompass a variety of things we need to know on the job - such as forensics, examining malicious binaries - and then making our own scripts.
First we need to understand the goals of malware. The purpose of malicious software can be mapped to its threat actor quite well, with lower level malware - reused by script kiddies etc - just being for the purpose of taking a particular target or service down. It is essentially malicious software, which could be anything - it really depends on what part of the infrastructure is weakest and thus scripts/programs will be written accordingly for that vulnerability. The most recent example would probably be the SolarWinds hack which was able to breach the monitoring software and impersonate users. Clever hackers can write scripts which are sent over botnets and they can swiftly scan millions of networks to check if they would be affected ...
From a business perspective we need to secure resources. We need to make sure that we have the proper logging mechanisms in place - we always want to know who has been in and out of our FTP servers for example, what they accessed and when they logged on. Other things we can do is attach checksums to individual files, which are essentially hashes - which are calculated based on the contents of that file, moreover if the contents were to change and we redid the hashing function on that file it would show a completely different hash. This technique is more formally known in the broader IT community as "verifying the integrity of a file". In networking, layer two communications (usually the Ethernet layer) will have a checksum trailer to allow the recipient on the other end to conduct a check on the packet - if it has changed during transmission then the checksum that comes with that packet is said to be corrupted and there needs to be a resending.
Online Sandboxing
Its a pretty appropriate name considering what it describes - a section cordoned off as the resulting content shouldn't go everywhere ! We cordon off malware within a slice of our computer, usually within a virtual machine or other type of jail so that if it does crash the system no biggie our underlying kernel is safe. However ! Malware nowadays is a lot smarter, and hackers keep libraries which have specialised at checking for signs of virtual testing , the signs of a researcher trying to gain our secrets, and if the library can deduce it is within a virtual machine it will either attempt to break free or completely shut down and erase itself.
It's not a bad idea that when you do find a brand-new piece of malware to put it through an online malware checker, so we can see if such facets of that software are prevalent in the code itself, such sites include:
An example any.run report can be seen here for the emotet malware:
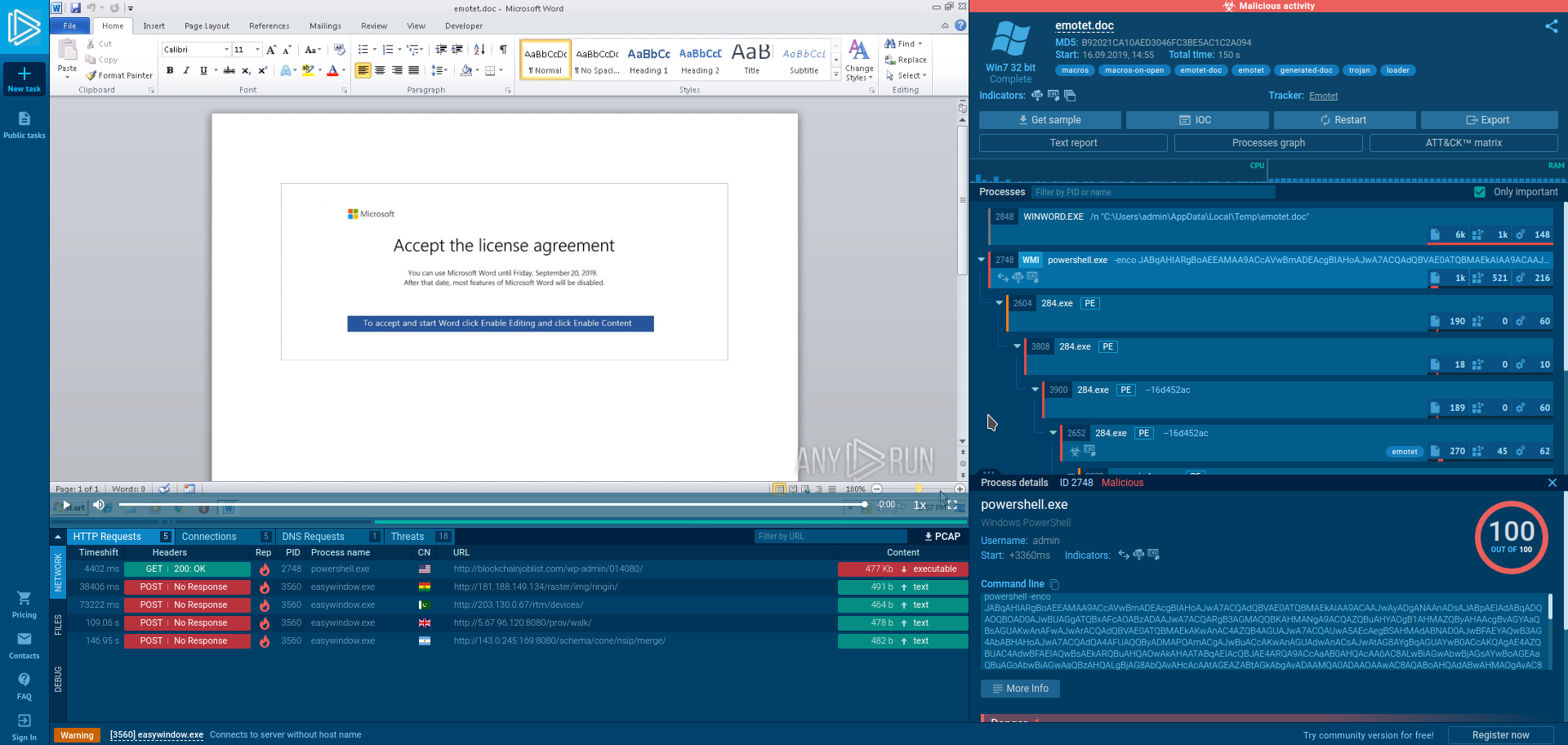
With these services we can learn how malware behaves at no detriment to ourselves, and we can take much weaker simple malware code that has already been run and put into jails ourselves. Thus we can build a picture in our minds about its functionality, what are the signature pieces of such an attack etc. Over time we will have the experience to know the "pain-points" of malware, as well as its goals and what parts of a system it will want to target.
Reverse engineering is another aspect of malware analysis, where the executable has been found and we can run it through something like radare which allows us to view the corresponding assembly code.
These platforms are only capable of executing malware and generating reports based upon interactions made with the operating system, any communication attempts and any signatures left behind. For example:
- Contacting a domain name (DNS Lookups, etc)
- Creating registry keys
- Read/Writing files
- Creating system processes
- Maintaining persistent through system startup entries
All of which are all discoverable by an analyst after some time. Therefore, online sandboxes are useful for a precursory inspection of a file.
Finding the hash of some files
Now then, back to the tryhackme box, let's see if we can get the hash from the loginform.exe file
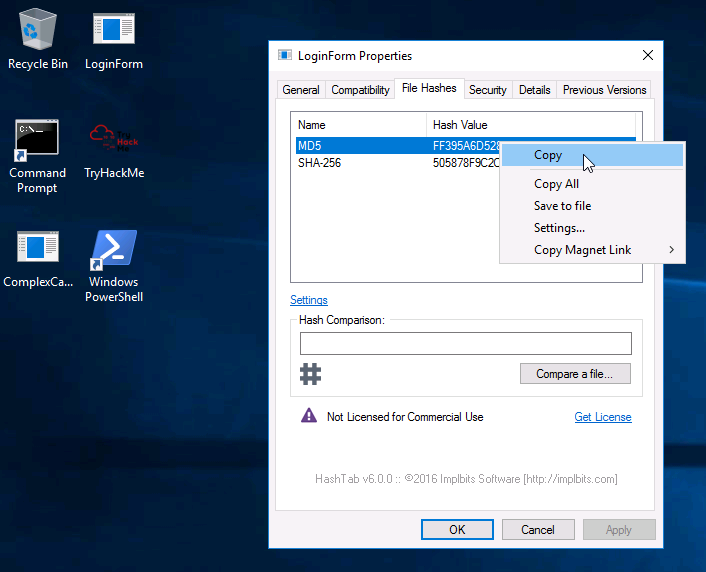
But we can also use powershell
Get-FileHash .\TryHackMe.exe
;; or the slightly more complex
CertUtil -hashfile .\TryHackMe.exe SHA256